Master of Science in Cyber Security
Cloud Security Architect Specialization
New Term Begins
6th April, 2026
Program Duration
2 Years
Number of Courses
12 (36 Semester Credits)
Learning Format
Online / Hands-On
Certifications Included
Up to 4
Achieve a Master’s Degree in Cyber Security and Lead as a Cloud Security Architect
With a curriculum that goes beyond traditional academic frameworks, EC-Council University integrates practical training with industry-recognized certifications, such as the Certified Ethical Hacker (CEH), Certified Cloud Security Engineer (CCSE), Certified Application Security Engineer (CASE), and Certified Network Defender (CND). This approach equips you with tangible skills and a competitive edge, enabling you to tackle cyber security challenges with confidence. This approach equips you with tangible skills and a competitive edge, enabling you to tackle cyber security challenges with confidence.
This advanced degree prepares you for 20+ cybersecurity roles, providing you expertise in cloud security implementation, network security management, penetration testing, and more. You’ll plan, analyze, design, configure, test, implement, maintain, and support cloud-based systems to ensure complete protection from sophisticated cyber attacks.
Master In-Demand Technical Expertise
Build Practical, Hands-on Skills
Advance with Management & Soft Skills Mastery
Admission Inquiry
Talk to Our Admission Counselor —we’re here to help you use your VA benefits
"*" indicates required fields
World-Class Cyber Security Education Focused on Cloud Security
Discover the True University Experience with ECCU
Gain In-Demand Skills to Advance as a Cloud Security Architect
Cloud Security
Acquire in-depth knowledge of cloud security concepts, cloud security architecture, and best practices. This knowledge is valuable for cloud security engineers, architects, and analysts.
Network Security
Develop your expertise in network protocols, configurations, and security measures, essential for various cyber security job roles.
Ethical Hacking and Penetration Testing
Sharpen your skills and knowledge of tools used for vulnerability assessment, pen testing, and ethical hacking.
Secure Coding Practices
Prevent cloud software vulnerabilities and mitigate cyber security risks at the development stage by mastering best practices for writing secure code.
Risk Management
Amplify your proficiency in identifying, assessing, and mitigating cybersecurity risks by understanding risk management principles and implementing strategies to safeguard organizations from cyber threats.
Soft Skills
Augment your technical skill set with improved communication, leadership, decision-making, problem-solving, and critical thinking capabilities.
Master of Science in Cyber Security - Cloud Security Architect Specialization
ECCU’s Master of Science in Cyber Security program with the Cloud Security Architect specialization consists of 8 foundational courses, 3 specialized courses, and 1 Capstone project.
Foundation Courses
ECCU 505 Introduction to Research and Writing (3 Credit Hours)
This course introduces you to basic English writing skills and research methods, including APA-style writing, citing sources, determining when a website is credible, and using effective business communication.
ECCU 504 Foundations of Organizational Behavior (3 Credit Hours)
This course deals with organizational behavior, allowing you to experience the basic facets of organizational theory and define the skills required to understand and apply the theory to real-world environments. Elements of the course are organizational structure, effective communication, team building, ethics, and project management, as seen through the organizational lens.
ECCU 514 Leadership and Management in Organizations (3 Credit Hours)
This course encompasses an extensive research project about cross-cultural differences in leadership conducted by a group of researchers in 62 countries. It lays a foundation for understanding the process of leadership. The study examines the roles, functions, and impact of global leadership concepts, along with team exercises that simulate the speed at which leaders must act. Research and views into how most cultures respond to this management area are also provided.
ECCU 516 The Hacker Mind: Profiling the IT Criminal (3 Credit Hours)
While cyberspace has increased human communication, connectivity, creativity, and capacity, it has also increased crime exponentially in the last decade. This crime aspect is exploited by everyone from hackers in high school to international terrorists. IT criminals threaten businesses, governmental agencies, militaries, and organizations of every kind. This course will survey the spectrum of psychological attributes that make up the profile of IT criminals.
MGMT 502 Business Essentials (3 Credit Hours)
This course provides a comprehensive foundation in business principles, equipping you with essential knowledge and skills applicable across various business environments. You’ll develop a strong understanding of key business concepts by exploring how successful entrepreneurs navigate global competition and evolving market dynamics.
ECCU 500 (CND Certification) Managing Secure Network Systems (3 Credit Hours)
This course evaluates network and IT security issues, designing and implementing successful security policies and firewall strategies, exposing system and network vulnerabilities, and defending against associated threats. Topics include network protocols, network attacks, intrusion detection systems, packet filtering, proxy servers, Bastion hosts and honey pots, hardening routers, hardening security, email security, virtual private networks, and creating fault tolerance.
ECCU 501 (CEH Certification) Ethical Hacking & Countermeasures (3 Credit Hours)
This course focuses on how perimeter defenses work, how intruders escalate privileges, and methods of securing IT systems. Additional topics include intrusion detection, policy creation, social engineering, DoS attacks, buffer overflows, and virus creation.
ECCU 507Linux Networking and Security (3 Credit Hours)
This course focuses on configuring a secure Linux network using the command line and graphical utilities. Emphasis is placed on file-sharing technologies such as the Network File System, NetWare’s NCP file sharing, and File Transfer Protocols. Additional topics include securing data, user security, file security, and network intrusion detection. You will take on the role of a problem solver and apply the concepts to situations that occur in real-world environments.
Specialized Courses (Select Any 3)
ECCU 520 Advanced Network Defense (3 Credit Hours)
This course focuses on the fundamentals of fortifying network defenses by discovering methods of developing a secure baseline. You will learn how to safeguard enterprise IT architecture from advanced cyber-attacks through segmentation and isolation techniques that reduce the effectiveness of persistent threats.
ECCU 524 (CCSE Certification) Designing and Implementing Cloud Security (3 Credit Hours)
This course provides comprehensive knowledge of cloud services and their characteristics, benefits, applications, and service models. It covers planning, designing, and implementing cloud security controls and delves into various cloud security standards, countermeasures, and best practices. This cloud security course also highlights the business aspects of cloud security, such as cloud uptime, uptime guarantee, availability, fault tolerance, failover policy, and how cloud security strengthens the business case for cloud adoption.
ECCU 525Cloud Security Platforms (3 Credit Hours)
This course shows you how to manage risk in cloud environments. It covers data protection, types of cloud-based service models, the right procedure for deploying every model, and dimensions of cloud security. You will learn to manage, configure, and implement cloud security services across most platforms. By the end of this course, you will be equipped with cloud security skills such as password management, role management, encryption, auditing, application control, access control, and centralized security monitoring.
ECCU 510 (CASE Certification) Secure Programming (3 Credit Hours)
This application security course encompasses security activities in all phases of the Software Development Lifecycle (SDLC). The course focuses on selecting and implementing the right security strategies, guidelines, and practices that are widely accepted and applicable in most cloud environments used today.
Capstone
ECCU 519 Capstone (3 Credit Hours)
The Capstone is a summative experience, allowing you to demonstrate all program outcomes by drawing on the knowledge and skills gained throughout the program. You can enroll in the Capstone after successfully completing all core degree requirements, but it must be within six semester credit hours of graduation. You must attain a cumulative grade point average of 3.0 and have the Registrar’s approval to undertake the Capstone.
Invest in Your Cyber Security Career
Your investment includes
- 12 in-depth courses
- Hands-on virtual practice labs
- Digital textbooks & instructional materials
- 360° academic advisory support
- Grammarly Pro subscription
- Industry-recognized certifications
New Term Starts On
April 6th, 2026
$1,620
Cost per Course
$19,440
Total Program Fee
A Degree That Offers Significant Returns on Investment
This cloud security degree empowers you to gain the advanced skills in architecting secure cloud infrastructures across sectors and meeting the rising demand for experts who defend organizations from cyber threats. You’ll master the most critical aspects of cloud-based cyber security, preparing you to step into high-impact roles that are vital in protecting cloud infrastructures.
Chart Your Earning Potential
1 in 2 ECCU graduates earn annual salaries of over $100,000 after completing the program.
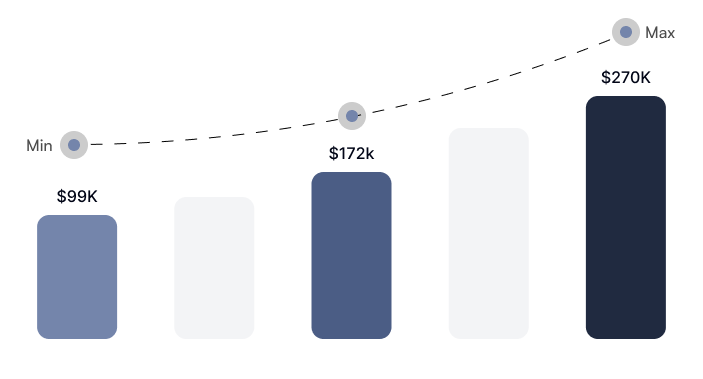
A Cloud Security Architect’s Salary Progression
Organizations offer highly competitive salaries and pay hikes to recruit and retain qualified professionals skilled in this vital cyber security discipline.
Watch how Linton Harris transformed his career after graduating from the program.
The Most Affordable Way to Upgrade Your Cyber Security Career
Flexible Payment Options
Financial constraints should not hinder your career aspirations. At EC-Council University, we offer flexible payment plans designed to accommodate your circumstances to support your career development, giving you peace of mind as you study on your own terms. Contact our Finance Team to explore payment solutions tailored to your needs.
Credit Transfer
Leverage your previous academic achievements by transferring credits—such as from an associate degree or other accredited academic programs—toward a master’s degree in cyber security at ECCU, allowing you to fast-track your program. Furthermore, if you hold relevant certifications, you may be eligible to convert this expertise into academic credits.
Scholarship Eligibility
At ECCU, we understand that the cost of higher education can be a challenge for many, which is why we offer a range of scholarships and grants to support your academic journey. For example, the Cyber Security Dean’s Scholarship is offered to deserving students who are academically gifted and dedicated to making their educational experience a successful endeavor.
Prepare for 20+ High-Demand Job Roles
- Cloud Security Architect
- Cloud Information Security Specialist
- Cloud Security Engineer
- Cloud Security Professional
- Cloud Security Analyst
- Cloud Support Consultant
- IT Analyst
- IT Support – Cloud
- Ethical Hacker
- Technical Support Specialist
- Computer Network Architect
- Network Operations Specialist
- Enterprise Architect
- System Administrator
- Security Architect
- Systems Security Analyst
- Systems Requirements Planner
- Chief Information Security Officer
- System Testing and Evaluation Specialist
- Information Security Officer
- Information Systems Security Developer
- Chief Security Officer
- Information Systems Security Developer
- Chief Security Officer
- Systems Developer
- Information Assurance Security Officer
View More…
View Less
Enhance Your Credentials
Graduate with a master’s degree and a string of EC-Council Certifications to raise your technical expertise and professional credibility.
Immerse Yourself in the Future of Online Learning
Immerse Yourself in the Future of Online Learning
Get the unrestricted advantages of ECCU’s acclaimed Learning Management System (LMS) when you join the Master of Science in Cyber Security program. Our platform offers a fluid and user-friendly UI that seamlessly integrates your library of learning resources and program activities into an engaging virtual classroom that you can access anytime, anywhere. Here’s what you’ll experience:

Live Sessions (30 Mins)

Courseware

Virtual Labs

Quizzes

Discussions

Essential Tools

24x7 Online Library

Capstone Projects

Assignments & Assessments
Accreditations and Recognitions




A Testament to Our
Academic Excellence
ECCU’s online cyber security programs are crafted to empower driven professionals to turn their aspirations into reality and achieve their career dreams.

93%
Employment Rate
ECCU graduates land jobs in leading organizations after completing the program.
82%
Report Career Enhancement
ECCU graduates mention that the programs have had a demonstrable impact on their career growth.
80%
Apply Training at Work
Graduates of ECCU say that the knowledge and skills acquired from the programs are regularly applied at work.
Our Alumni are Making an Impact at the World’s Leading Organizations Across Sectors
Work Alongside Our Alumni in Top Companies
JP Morgan
Pfizer
Apple
Microsoft
Accenture
Amazon
IBM
Lead in Key Industries
Technology
Finance
Healthcare
Education
Manufacturing
Government
Aerospace
Non-Profits
Retail

From Learning to Leading - Your Roadmap to Success
01
Application
Submit the application form along with relevant documents for this online cyber security master’s degree.
02
Evaluation
The Admissions Team evaluates your documents, transcripts, and diplomas to determine eligibility.
03
Registration
Sign the official Student Enrollment Agreement after paying the tuition fee.
04
Orientation
Attend an online orientation session that guides you through the program.
05
Program Completion
Clear the final exams of each course, accompanying assessment, and the Capstone project to acquire credits.
06
Cyber Security Certifications
Earn up to 4 industry-recognized EC-Council certifications.
07
Graduation Ceremony
Graduate with your master’s degree in cybersecurity.
08
Career Guidance
Get expert career guidance and resume-building assistance from ECCU.
Your Admission, Made Simple
Experience a seamless and hassle-free admission process when you enroll in this program. From your first question to your first class, our dedicated Enrollment Advisors are here to guide you every step of the way.
What You’ll Need
Depending on where you’re applying from and your academic background, you might be asked to submit:
Official transcripts of prior education
Valid government identification
Completed application form
Application fee payment
Proof of English language proficiency (if applicable)
Not sure what applies to you? No worries - help is just a click away!
Visit our
Frequently Asked Questions
Q. What is the role of a cloud security architect?
A cloud security architect designs and implements cyber security tools and strategies for cloud-computing systems and infrastructure effectively. They protect sensitive data stored in cloud-based environments while ensuring optimal performance and scalability.
Q. How can I become a cloud security architect?
Your path to a rewarding career as a cloud security architect starts by joining EC-Council University’s Master of Science in Cyber Security program with the Cloud Security Architect specialization. This program equips you with all the skills you need to become a highly qualified cloud security professional.
Q. What are the primary skills needed to become a cloud security architect?
To become a cloud architect, you need to have the following primary skills and requirements:
- A strong background in cloud computing
- Knowledge of computer programming languages
- Digital security skills
- A good understanding of IT networks
- Familiarity with at least one operating system
Q. How much do cloud architects make?
The total yearly salary for Cloud Security Architects in the U.S. ranges from $99,000 to $270,000, with a median pay of $172,000.
(*Please Note – Source: Payscale.com. EC-Council University does not guarantee the salary details mentioned above. The salary will be influenced by factors including but not limited to experience, industry, location, and bonuses.)
Q. Can I pursue this Cloud Security Architect degree while working a full-time job?
Yes! Most of our students work full-time and manage their studies by learning in the evenings and on weekends. When pursuing ECCU’s Master of Science in Cyber Security, Cloud Security Architect specialization, you should plan to dedicate 10 to 12 hours per week per class. Depending on your schedule, you can take one or two classes per term to balance work and studies effectively.

