Bachelor of Science in Cyber Security
Your Gateway to Cyber Security Career Excellence
Your Gateway to Cyber Security Career Excellence

"*" indicates required fields



Develop your expertise in network protocols, configurations, and security measures, essential for various cyber security job roles.





Access a robust learning framework when you join ECCU’s Bachelor of Science in Cyber Security program.


Access a robust learning framework when you join ECCU’s Bachelor of Science in Cyber Security
Courses that offer an in-depth study of crucial cyber security domains.
Courses that deepen your expertise in core technical disciplines of cyber security.
Courses that expand your business acumen and communication skills.
The summation of your learning journey to test your newly acquired knowledge and skills.
The program’s curriculum features 20 expansive courses taught by ECCU’s globally renowned faculty of cyber security professors.
This course explores the complex landscape of information systems security. You’ll gain a thorough understanding of the various issues that jeopardize the availability, confidentiality, and integrity of digital assets. The curriculum covers the core concepts, terminology, and elements underpinning effective security practices, aligning with industry standards and best practices.
This course examines areas where law and cyber security concerns intersect. Information systems security and legal compliance are now required to protect critical governmental and corporate infrastructure, intellectual property created by individuals and organizations alike, and information individuals believe should be protected from unreasonable intrusion.
This course provides an in-depth exploration of managing risk within information systems by leveraging cyber threat intelligence. You will examine core concepts of cyber threat intelligence and its critical role in risk management. The course will guide you through the stages of a cyber-attack, helping you identify vulnerabilities and design effective defensive strategies.
* You can attempt the Certified Threat Intelligence Analyst (CTIA) certification exam after completing this course.
This course provides an overview of security administration and the fundamentals of designing security architectures. Topics include security policy creation and enactment lifecycles, policy structure and frameworks, security policy management and implementation, compliance laws, and security policy enforcement.
This course focuses on helping you acquire the skills, knowledge, and capabilities to make valuable contributions to a SOC team. It covers the fundamentals of SOC operations, log management and correlation, SIEM deployment, advanced incident detection, and incident response. Additionally, you will learn to manage various SOC processes and collaborate with CSIRT during times of need.
* You can attempt the Certified SOC Analyst (CSA) certification exam after completing this course.
This course defines access control components, provides a business framework for implementation, and addresses legal requirements that impact access control programs. It looks at the risks, threats, and vulnerabilities prevalent in information systems and IT infrastructures and how to handle them. It details how to operate, test, and manage access control systems.
This course equips you with the skills to analyze internal and external security threats to organizational networks. You will learn how to create and implement security controls and policies to mitigate security threats. Key topics include network security, hacking methodologies, defense countermeasures, virtualized IT environments, and cyber threat intelligence.
* You can attempt the Certified Network Defender (CND) certification exam after completing this course.
This course gives you deep insights into the current cyber security landscape and the types of sophisticated attacks on IT systems conducted by cyber-criminals. By learning to think like a malicious actor, you’ll know how to take pre-emptive measures and thwart cyber-attacks before they occur.
* You can attempt the Certified Ethical Hacker (CEH) certification exam after completing this course.
This course empowers your understanding of system forensics, investigation, and incident response. It covers key concepts in digital evidence collection, strict data handling, and forensic acquisition techniques. You will explore tools and methods for electronic data recovery, disk drive characteristics, and file system analysis using Autopsy and Sleuth Kit. The course also addresses advanced topics like file carving, anti-forensic techniques, network forensics, and investigation of email, web applications, databases, and mobile devices.
* You can attempt the Computer Hacking Forensic Investigator (CHFI) certification exam after completing this course.
Select Any 5 of the Following Courses
This course helps you understand the cyber security threats to Microsoft Windows OS and how to protect it from attackers. You’ll learn to create and maintain a secure environment by finding and mitigating vulnerabilities in Windows OS systems.
This course is an introduction to securing Linux platforms and applications. Areas of study include identifying and examining methods of securing Linux platforms and applying and implementing those methods.
This course addresses how the Internet and web-based applications have transformed the way businesses, organizations, and people communicate. With this transformation came new risks, threats, and vulnerabilities for web-based applications and people who use them. This course presents security strategies to mitigate the risks associated with web applications and social networking.
This course explores the cyber warfare landscape, offensive and defensive cyber warfare techniques, and the future of cyber warfare. It also addresses military doctrine, strategies, intelligence operations, and cyber warfare laws and ethics. You will be exposed to cyber security technologies, processes, and procedures that protect endpoints, networks, and data. You will also learn to identify and analyze threats and vulnerabilities to create appropriate mitigation strategies.
This course explores the evolution of wired to wireless networks and its impacts. Through case studies of real-world events, the course examines risk assessments, threats, and vulnerabilities of wireless networks, as well as the security measures that should be implemented to mitigate breaches.
This course focuses on the analysis and design of fundamental data structures and algorithms for manipulating them. You will use data structures to design efficient computer programs. Topics include linked lists, array-based lists, hash tables, recursion, binary tree, red-black trees, heaps, sorting algorithms, and graphs.
This course teaches you the fundamentals of research and writing, such as determining if a website is credible/trustworthy, writing tips and strategies, critiquing, preparing research papers/articles, designing an outline, developing a thesis statement, writing a conclusion, and referencing your work.
Select Any 4 of the Following Courses
This course introduces you to the principles of ethics (moral philosophy) through various topics and dilemmas. You will learn about ethical theories and apply this knowledge to current events to better understand morality, obligation, human rights, and human nature.
This course covers the economic study of how people make decisions, how they work, what they buy, how much they save, how they invest those savings, and how they interact with others. The course analyzes forces and trends affecting the economy, including income growth, the section of the population who cannot work, and the rate at which prices rise or fall.
This course gives you a strong understanding of IT project management as you learn to apply the most effective tools and techniques. The course helps you prepare for the Project Management Professional (PMP) or Certified Associate in Project Management (CAPM) exams. It also goes beyond the PMBOK® Guide to offer a meaningful context for IT project management.
This course will familiarize you with a broad base of concepts related to probability and statistical methods. You will learn to collect, analyze, and interpret numerical data and descriptive statistics, create basic probability models, and use statistical inference. This course helps you understand how to interpret and critically analyze research data and apply statistical reasoning and interpretation.
This course introduces you to the field of social psychology, but more specifically, to understand how other people influence our behaviors. It provides a general overview of human behavior in a social matrix. It also explores topics and concepts such as social psychology research, the self, prejudice and discrimination, attraction, relationships, aggression, socialization, and conformity.
This course comprehensively assesses your knowledge and skills in information systems and cyber security. Activities include researching selected security problems and planning, designing, and implementing security solutions for an organization.
Our online bachelor’s degree in cybersecurity gives you a solid foundation of skills and knowledge to protect an organization’s data and information systems from sophisticated cyber-attacks, positioning you for success in numerous cyber security job roles.
1 in 2 ECCU graduates earn annual salaries of over $100,000 after earning a cybersecurity degree.
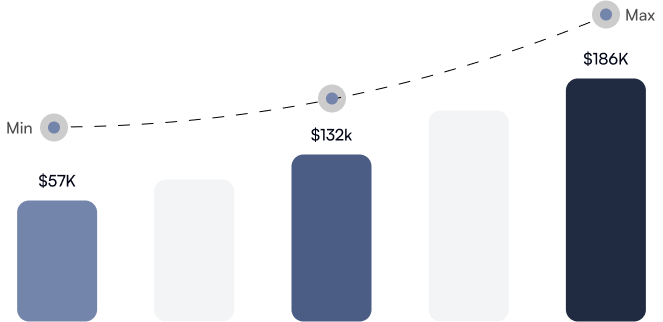
Organizations offer highly competitive salaries and pay hikes to recruit and retain qualified professionals skilled in vital cyber security disciplines.
Watch how Linton Harris increased his earnings after graduating from ECCU.
Financial constraints should not hinder your career aspirations. At EC-Council University, we offer flexible payment plans designed to accommodate your circumstances to support your career development, giving you peace of mind as you study on your own terms. Contact our Finance Team to explore payment solutions tailored to your needs.
Leverage your previous academic achievements by transferring credits—such as from an associate degree or other accredited academic programs—toward a bachelor’s degree in cyber security at ECCU, allowing you to fast-track your program. Furthermore, if you hold relevant certifications, you may be eligible to convert this expertise into academic credits.
At ECCU, we understand that the cost of higher education can be a challenge for many, which is why we offer a range of scholarships and grants to support your academic journey. For example, the Cyber Security Dean’s Scholarship is offered to deserving students who are academically gifted and dedicated to making their educational experience a successful endeavor.
… And Many More!
Graduate with an online cyber security bachelor’s degree and a string of EC-Council certifications to raise your technical expertise and professional credibility.



Get the unrestricted advantages of ECCU’s acclaimed Learning Management System (LMS) when you join the Bachelor of Science in Cyber Security program. Our platform offers a fluid and user-friendly UI that seamlessly integrates your library of learning resources and program activities into an engaging virtual classroom that you can access anytime, anywhere. Here’s what you’ll experience:














ECCU’s online cyber security programs are crafted to empower driven professionals to turn their aspirations into reality and achieve their career dreams.
ECCU graduates land jobs in leading organizations after completing the program.
ECCU graduates mention that the programs have had a demonstrable impact on their career growth.
Submit the application form along with relevant documents for this online cyber security bachelor’s degree.
The Admissions Team evaluates your documents, transcripts, and diplomas to determine eligibility.
Graduate with your bachelor’s degree in cyber security.
Get expert career guidance and resume-building assistance from ECCU.
Experience a seamless and hassle-free admission process when you enroll in this program. From your first question to your first class, our dedicated Enrollment Advisors are here to guide you every step of the way.
Depending on where you’re applying from and your academic background, you might be asked to submit:
If you want to raise your career profile by becoming a highly skilled cyber security professional, you need to have a bachelor’s degree in cyber security. According to a recent report from Burning Glass, 88% of cyber security job postings specify a bachelor’s degree or higher as an important requirement for candidates.
A bachelor’s degree in cyber security is ideal if you wish to begin a career in cyber security. EC-Council University’s Bachelor of Science in Cyber Security is a great choice as it features a comprehensive curriculum that explores crucial aspects of modern cyber security, provides flexible and experiential learning from a faculty of industry experts, virtual lab environments to practice using the latest cyber security tools and techniques, and offers up to 5 industry-recognized certifications that enhance your cyber security capabilities and credentials.
Yes, it is. A cyber security bachelor’s degree paves the way toward career success in an industry where employers offer lucrative salaries to qualified professionals. Given the stark shortage of cyber security talent, the demand for such professionals is constantly increasing. ECCU’s Bachelor of Science in Cyber Security degree can transform you into a coveted cyber security professional, accelerate your career growth, and help you capitalize on this industry trend.
Enrolling in our Bachelor of Science in Cyber Security program is a fairly simple process. However, you must meet certain criteria to be eligible for admission. Please see the ‘Admission Requirements’ section or visit our Admissions page for more details.
ECCU’s Bachelor of Science in Cyber Security program is a 2-year online program featuring 20 courses with a combined value of 60 credit hours.
ECCU’s Bachelor of Science in Cyber Security program includes up to 5 industry-recognized cyber security certifications. You can earn these certifications upon successfully completing the corresponding courses. Here is the list of the certifications available:
1. Certified Threat Intelligence Analyst (CTIA)
2. Certified Ethical Hacker (CEH)
3. Certified SOC Analyst (CSA)
4. Certified Network Defender (CND)
5. Computer Hacking Forensics Investigator (CHFI)
Students are evaluated on their participation in discussion threads, assignments, lab assessments and reports, final examinations, papers, course final projects, and the Capstone course.
"*" indicates required fields
"*" indicates required fields