Advanced Technologies Need Advanced Cybersecurity Measures
Digital transformation is advancing at breakneck speed, with applications in smart homes, industrial control systems, healthcare devices, transportation, and entire cities. However, cybersecurity in these areas has often failed to keep pace. Traditional cybersecurity models, built around protecting monolithic servers, desktops, and corporate networks, struggle to adapt to the sprawling, distributed, and heterogeneous landscape shaped by the convergence of Internet of Things (IoT), 5G networks, and Edge Computing. This leaves us facing a stark reality – cyber threats are evolving faster than many organizations can adapt.
In this article, we explore how IoT, 5G, and edge computing amplify cyber risks, define their key features, examine emerging vulnerabilities, and highlight how EC-Council University (ECCU) is empowering the next generation of cybersecurity professionals to tackle these advanced threats.
IoT, 5G, and Edge Computing: What They Are and What They Do
Here’s a quick overview that distills the core features of IoT, 5G, and edge computing:
- IoT: At its core, IoT refers to the vast ecosystem of physical devices (sensors, actuators, smart appliances, industrial controllers, wearables, vehicles) that connect to the internet and exchange data. These devices collect information, communicate with one another or centralized servers, and often act on sensor input or remote commands. Because IoT spans personal devices (such as smartphones and smart home gadgets) to industrial-grade sensors (such as smart-grid meters and factory robotics), it introduces a highly distributed, diverse, and resource-constrained digital environment.
- 5G: 5G is the next-generation wireless communications standard that enables ultra-low latency, high bandwidth, massive device density (potentially millions of connected devices per square kilometer), and flexible network architectures. It supports a convergence of use cases, from smart-city sensors and autonomous vehicles to real-time video, remote control systems, and massive IoT deployments. 5G often uses virtualization, software-defined networking (SDN), and network function virtualization (NFV) to deliver scalable, flexible services.
- Edge Computing: Edge computing brings computation and data storage closer to where data is generated (e.g., on or near IoT devices, local gateways, or edge servers) rather than sending everything to centralized cloud data centers. This reduces latency, conserves bandwidth, and enables real-time processing and decision-making (critical for applications like autonomous vehicles, industrial automation, and remote healthcare). Edge computing complements 5G and IoT by allowing fast, local processing of massive data streams.
Together, IoT, 5G, and edge computing form a powerful triad that fuels today’s digital transformation, while also dramatically increasing cyberattack vectors and creating new headaches for cybersecurity professionals.
Key Cybersecurity Challenges Across IoT, 5G, and Edge Computing
IoT: Expanding the Digital Attack Surface
Why IoT Is Hard to Secure
- IoT devices often have limited processing power, memory, or battery life. They may not support strong encryption, robust authentication, or endpoint-protection software.
- The IoT ecosystem comprises devices from numerous vendors, each with distinct firmware, communication protocols, and security standards. This heterogeneity complicates centralized security management.
- Devices like smart meters or industrial sensors may remain operational for many years, but security updates and patches often don’t keep pace. Once unsupported, they remain permanently weak links.
- IoT devices constantly send and receive data; if one device is compromised, attackers may use it as a pivot point to infiltrate larger networks.
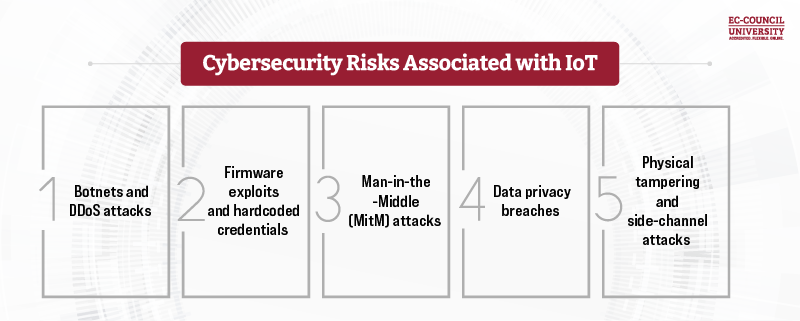
Prominent IoT Cybersecurity Threats
- Botnets and DDoS attacks: The infamous 2016 Mirai botnet exploited thousands of insecure IoT devices to launch massive DDoS attacks against major websites such as Twitter and Netflix, showing how IoT devices can be weaponized on a global scale.
- Firmware exploits and hardcoded credentials: Many IoT devices ship with default or weak credentials or run outdated firmware. Attackers exploit these flaws to gain persistent access, establish backdoors, or manipulate device behavior.
- Man-in-the-Middle (MitM) attacks: IoT communications often traverse weakly encrypted or unencrypted channels, making them vulnerable to interception, tampering, or eavesdropping.
- Data privacy breaches: IoT devices collect enormous amounts of personal and operational data (location, usage patterns, biometrics, health metrics, sensor data), which attackers can steal, sell, or misuse for identity theft and extortion.
- Physical tampering and side-channel attacks: Unlike purely virtual assets, IoT devices exist in a physical form. Threat actors may physically access or reverse-engineer devices to extract firmware, encryption keys, or proprietary code.
Given this broad and growing threat landscape, protecting IoT requires a security-first, multi-layered, and continuous approach. For an in-depth examination of all facets of cybersecurity for IoT, read: Cybersecurity for IoT: Best Practices to Defend Against Evolving Threats.
5G Networks: The New Playground of Fast Connectivity and Bigger Risks
Why 5G Changes the Cybersecurity Game
- The architecture of 5G departs from traditional centralized, hardware-based switching to distributed, software-defined, virtualized routing. This decentralization blurs once-clear security perimeters.
- 5G networks support massive numbers of connected devices, including IoT devices. This scale (millions of endpoints per square mile) dramatically increases potential entry points.
- 5G introduces advanced features like network slicing (virtual network partitions), edge computing integration, and software-based network functions, all of which carry novel risk vectors.
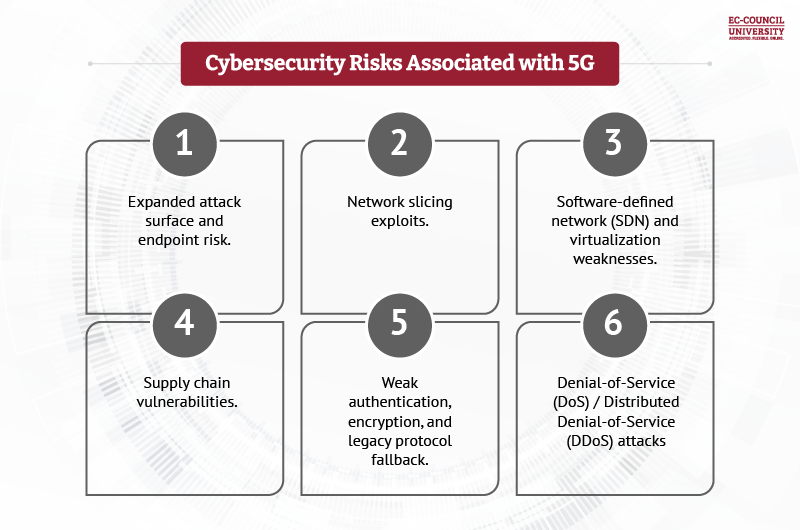
Key Vulnerabilities and Risks in 5G Network Security
- Expanded attack surface and endpoint risk: A single compromised 5G-connected device (such as a sensor or IoT appliance) can become the gateway for wider network infiltration.
- Network slicing exploits: Poorly isolated or misconfigured slices may allow attackers to breach one slice (e.g., IoT devices) and pivot into more sensitive slices (e.g., critical infrastructure or enterprise data).
- Software-defined network (SDN) and virtualization weaknesses: The shift to virtualized, cloud-like infrastructure makes the 5G core and control planes vulnerable to misconfigurations, software flaws, container or API exploits, and unauthorized access.
- Supply chain vulnerabilities: 5G hardware and software often come from multiple global vendors, increasing the risk that compromised components, like base stations, network functions, and firmware, enter the infrastructure unnoticed.
- Weak authentication, encryption, and legacy protocol fallback: While 5G improves many security aspects, in practice, many deployments still rely on weaker fallback protocols or fail to fully enforce end-to-end encryption, leaving gaps for interception, spoofing, or man-in-the-middle (MitM) attacks.
- Edge computing risks and decentralized infrastructure: Because 5G often pairs with edge computing, vulnerabilities at edge nodes (which may lack physical security, strong access controls, or patching) can expose sensitive data or network controls to attackers.
- Denial-of-Service (DoS) / Distributed Denial-of-Service (DDoS) attacks:The scale and speed of 5G can make DoS/DDoS attacks more potent, potentially crippling critical services or infrastructures such as healthcare, transportation, or utilities.
5G network security isn’t just about protecting mobile communications. It’s about defending a complex ecosystem of devices, networks, edge nodes, and applications, all operating at massive scale.
Edge Computing: Where Low-Latency Meets High-Risk
Why Edge Computing Complicates Cybersecurity
- Unlike central cloud data centers, edge nodes can reside in physically insecure or remote locations, making them susceptible to physical tampering or unauthorized access.
- Edge nodes may run different operating systems, firmware versions, and configurations, increasing the complexity of securing and maintaining them.
- Edge environments often handle sensitive, time-critical data (e.g., industrial control, autonomous systems, healthcare), meaning a breach can have immediate real-world consequences.
- Traditional security tools, designed for centralized cloud or enterprise infrastructure, may not work or scale well across dozens, hundreds, or thousands of distributed edge nodes, making consistent monitoring, patching, and threat detection difficult.
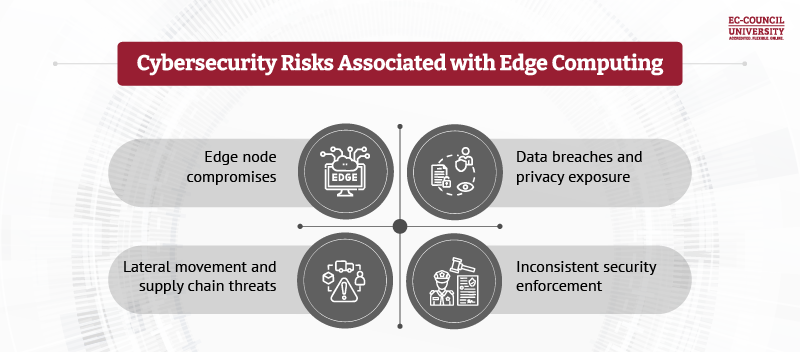
Edge Computing Security Risks
- Edge node compromise: Attackers who gain physical or remote access to edge nodes may manipulate data, inject malicious code, or disrupt services. Given the localized nature of edge computing, such compromises can lead to cascading failures across connected systems.
- Data breaches and privacy exposure: Sensitive data processed at edge nodes — real-time sensor data, health readings, video streams, telemetry — can be intercepted or exfiltrated if encryption and access controls are weak or misconfigured.
- Lateral movement and supply chain threats: A compromised edge node may serve as a pivot point to other parts of the network. Additionally, vulnerabilities in hardware or firmware may stem from supply chain issues, especially if vendors lack secure manufacturing or update practices.
- Inconsistent security enforcement: Because edge computing often involves many small, autonomous nodes, ensuring uniform patching, compliance, and security hygiene becomes a huge operational challenge.
Edge computing offers powerful capabilities, but only if organizations prioritize edge computing security as a primary concern, not an afterthought. Watch this comprehensive explainer on how to approach edge computing security: Improving Security and Scalability with Blockchain and Edge Computing.
ECCU’s Mission: Preparing Cybersecurity Professionals for the Next Frontier
The rapidly shifting cybersecurity landscape requires a new kind of professional, one who understands the complex interplay between IoT, 5G, and edge computing, as well as traditional network and application security. Here’s how EC-Council University (ECCU) empowers cybersecurity professionals to adapt to these changing circumstances:
- ECCU offers online degree and certificate programs, including bachelor’s and master’s degrees in Cybersecurity, that equip students with skills in network security, ethical hacking, penetration testing, secure programming, digital forensics, risk management, and much more. These programs are designed to address modern, real-world cybersecurity challenges.
- ECCU’s programs emphasize proactive and adaptive cybersecurity, promoting approaches like continuous monitoring, segmentation, and zero-trust architecture. These aspects are essential for guarding IoT, 5G, and edge computing environments.
By fostering deep technical knowledge, real-world skills, and strategic thinking, ECCU aims to prepare the next generation of cybersecurity professionals to defend our increasingly connected, integrated, and evolving digital world.
Why Continuous Learning and Upskilling are Essential
As we’ve established, IoT, 5G, and edge computing go beyond incremental technological advancements. They represent a paradigm shift in how we build, deploy, and interact with digital systems. While this transformation brings powerful capabilities, it also dramatically increases complexity and risk. No single security solution can protect an ecosystem this vast and dynamic. To outwit sophisticated cybercriminals, cybersecurity professionals must commit to continuous learning, proactive threat intelligence, and adaptable security postures.
ECCU stands at the forefront of this educational imperative. With globally recognized programs and certifications and a mission to develop future-ready cybersecurity leaders, ECCU enables learners to master emerging technologies and defend critical infrastructure before cyber threats exploit their vulnerabilities. As the world embraces the full potential of IoT, 5G, and edge computing, the need for well-trained, vigilant, and forward-thinking cybersecurity professionals has never been greater.
For more information on ECCU’s upskilling programs:







