Why 2026 Is the Year of AI-Powered Scams Going Mainstream and How to Survive Them
The New Era of Human-Centric Cyber Threats
Cybersecurity has entered a new era, one where humans, not systems, are the primary attack surface. Despite billions of dollars spent on firewalls, endpoint protection, and cloud security, social engineering remains one of the most effective attack vectors. Why? Because attackers don’t need to break code when they can exploit trust, urgency, fear, and authority.
What has changed dramatically is scale and sophistication. Social engineering isn’t new; cybercriminals have manipulated human psychology for decades. But today, with Generative AI powering fraud at scale, social engineering attacks have become smarter, faster, and difficult to detect. With generative AI, attackers can now launch highly personalized, emotionally intelligent, and convincingly human attacks at machine speed.
In 2026, phishing emails will not just be detected based on spelling and grammatical errors. We are facing real-time, believable impersonations, deep-fake voices, and emotionally charged scams crafted by machines. From deepfake CEOs to AI-crafted phishing conversations, social engineering is a precision-level psychological warfare.
Let’s dive into what has changed, the latest incidents shaking the cybersecurity world, and how you can stay ahead with cybersecurity upskilling.
A Brief Evolution of Social Engineering Attacks
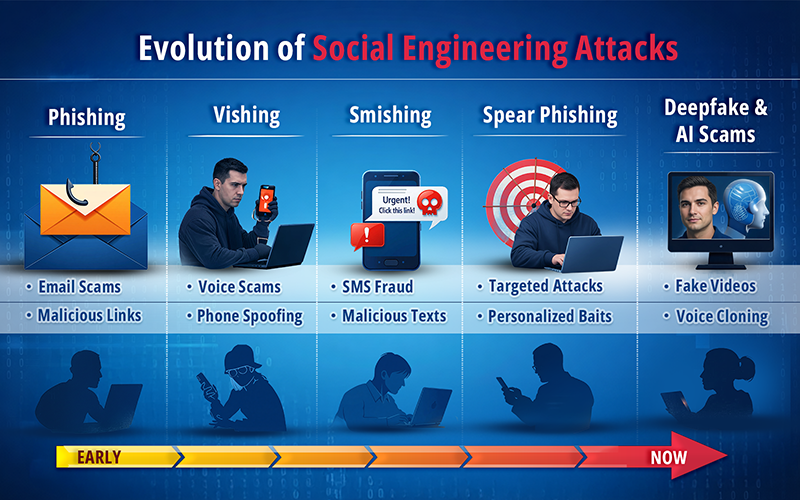
Social engineering has evolved alongside technology, but the main target has always remained the same: exploiting human behavior.
- Early days: Generic phishing emails with obvious red flags
- Next phase: Spear phishing and business email compromise (BEC)
- Today: Multi-channel, AI-powered deception using voice, video, chat, and social media
Attackers learned early that people are easier to exploit than systems. Generative AI has supercharged a proven strategy, making attacks more believable, scalable, and challenging to detect.
What Makes AI-Driven Social Engineering Different?
Traditional scams had poor grammar, suspicious sender addresses, and generic messages, which were much easier to detect and flag. But today, Generative AI changes the game in three significant ways:
✔ Hyper-realistic impersonation voices and faces that are nearly indistinguishable from real people.
✔ Hyper-personalization scams tailored using data scraped from social profiles and public sources.
✔ Automation and scale, wherein one attacker can deploy thousands of convincing fake messages in minutes.
In fact, industry experts explain that AI has made social engineering harder to detect because of the old warning signs — typos and unrealistic language things of the past.
How Generative AI Is Powering Smarter Social Engineering

Generative AI enables attackers to:
- Mimic natural human language flawlessly
- Analyze publicly available data to personalize messages
- Adapt conversations in real-time
- Automate attacks without sacrificing quality
AI does not just assist attackers, but it also thinks like them. It understands the tone, context, and emotional triggers, making social engineering attacks feel authentic rather than scripted.
This shift has blurred the line between legitimate communication and malicious intent, erasing many of the traditional warning signs users relied on.
Rise of Deepfakes, Voice Cloning, and Synthetic Identity Threats: Trends That Tell the Story
According to recent cybersecurity reporting:
- AI-powered attacks have jumped sharply, with 75% of security pros blaming AI for the increase in cybercrime. – (source: Tech Business News)
- Generative AI will continue dominating scams through 2026 — especially phishing and impersonation.
This means anyone online, from enterprise executives to everyday consumers, is a target.
One of the most alarming developments is the rise of deepfake-enabled social engineering.
- Voice Cloning Scams impersonating executives, government officials, or family members
- Deepfake Video Meetings are convincing employees to authorize financial transactions
- Synthetic Identities combining real and fake data to bypass identity verification
These attacks don’t rely on malware; they rely on belief. When employees see and hear someone they trust, skepticism drops. AI exploits this instinct perfectly.
High-Profile AI-Powered Social Engineering Incidents
Deepfake frauds are going industrial. A new 2026 study found that deepfake-based fraud is now happening on an industrial scale, not occasionally, but constantly.
Here are some of the most shocking and instructive real-world cases:
- HK$18.5M AI Voice Crypto Scam (Jan 2025)
In Hong Kong, fraudsters turned AI-generated voice cloning to devastating effect by impersonating a company’s finance manager on WhatsApp. This voice deepfake scam convinced the victim to transfer about HK$145 million (~$18.5M USD) into fraudulent crypto accounts.-International Daily Mirror
- Maine Town Officials Duped by Deepfake Voices
In another AI-enabled scam, municipal staff in Maine were tricked into believing deepfake voice messages and highly targeted phishing emails were legitimate instructions from their own officials — leading to unauthorized financial transfers. –Mainewire
- CFO Deepfake Fraud — $25.6M Loss
One of the most notorious cases involves employees at a multinational firm attending a video call where every participant except them was an AI-generated deepfake. Trusting what they saw and heard, they authorized transfers totaling $25.6 million. –CNN
- Voice Authentication Bypassed via AI
Even biometric voice systems aren’t safe. In 2025, hackers used deepfake audio to bypass bank voice authentication systems in Hong Kong, enabling unauthorized withdrawals totaling tens of millions before detection.- (security daily review)
The New Social Engineering Playbook
AI is allowing attackers to blend multiple techniques into a single, convincing attack:
Text, Voice, Video Scams
Where once phishing was just email, now attackers combine:
- Persuasive AI-generated emails
- Deepfake voice calls (vishing)
- Video impersonation in meetings
These layered attacks make detection extremely hard and increase the likelihood of success.
Emotion-Powered Scams
Scammers aren’t just random anymore; they exploit human emotions:
- Fake epidemic alerts
- AI-cloned voices of loved ones in distress
- Synthetic video threats demanding ransom
The emotional engineering element makes defenses even more challenging.
Social Engineering Beyond Email
Email is no longer the primary battlefield.
1. AI-Driven Attacks Across New Channels
Attackers are increasingly using:
- Messaging apps like WhatsApp, Telegram, and Signal
- Social media platforms such as LinkedIn and Twitter
- Collaboration tools like Microsoft Teams and Slack
These platforms feel informal and trusted, making users more likely to comply quickly — exactly what attackers want.

2. Blended Attacks: Humans + Technology
Modern attacks often combine:
- Legitimate credentials obtained through manipulation
- Technical exploits are triggered after trust is established
- AI-generated conversations that guide victims step-by-step
Why Perimeter Defenses Are No Longer Enough
Zero-day exploits get headlines, but credential misuse and human error cause far more damage. When attackers log in legitimately, traditional perimeter defenses become irrelevant.
Why Traditional Security Awareness Training Falls Short
Most security awareness programs are:
- Static
- Compliance-driven
- Focused on outdated threat models
AI-driven social engineering is adaptive and dynamic, while traditional training is not. Teaching users to “look for spelling mistakes” doesn’t work when AI produces flawless, contextual communication.
Security education must now focus on:
- Behavioral analysis
- Psychological manipulation techniques
- Real-world AI-powered attack scenarios
How to Defend Against AI-Enhanced Social Engineering

Defending against AI-driven attacks requires a strong human-centric security strategy:
- Continuous training using real-world simulations
- Multi-factor verification for sensitive actions
- Out-of-band authentication for high-risk requests
- AI-assisted detection tools to identify synthetic content
- Zero Trust mindset to verify everything, regardless of familiarity
Organizations must assume that any communication channel can be compromised.
Real-World Defense Strategies
1. Educate and Simulate
Train staff and family members to verify verbally before acting — a quick voice or video check can prevent even sophisticated deep-fake scams.
2. Multi-Factor Verification
Use out-of-band confirmation:
✔ separate phone calls
✔ secondary messaging apps
✔ secure identity tokens
3. AI Tools for Detection
There are emerging AI tools that help detect deepfakes and synthetic content, as AI is one of the best defenses against AI attacks.
4. Zero Trust Mindset
Never trust, always verify identity and source independently.
What Skills Cybersecurity Professionals Need in the AI Era

The AI era demands more than technical expertise. Cybersecurity professionals must understand:
- Human psychology and decision-making
- AI-driven threat modeling
- Adversarial use of generative technologies
- Risk assessment in hybrid human-machine environments
The future cybersecurity leader is not just a technologist but a strategic thinker who understands people, AI, and risk together.
How EC-Council University Prepares Professionals for AI-Driven Threats
EC-Council University equips professionals to meet this challenge head-on by blending:
- Cutting-edge cybersecurity education
- AI-focused threat intelligence
- Hands-on labs and real-world scenarios
- Curriculum aligned with evolving attacker techniques
You learn how attacks work, and why they succeed — a critical distinction in defending against social engineering in the age of AI.
The Future Is Human + AI Awareness
As AI continues to evolve, so will the scams. In the age of generative AI, cybersecurity is no longer just a technical problem but a human one. Here, awareness is your superpower. By understanding how attackers use generative tools to manipulate trust, you can stay one step ahead.
The battle between AI-driven fraudsters and defenders is heating up in 2026, but with the right combination of technology and training. Defending against social engineering requires:
- Continuous learning
- Adaptive thinking
- A deep understanding of AI-enabled threats
Organizations that invest in people, education, and future-ready skills will stay ahead. Those that don’t fall behind, not because their systems failed, but because trust was exploited.
Stay ahead of AI-powered social engineering threats with EC-Council University’s future-ready online cybersecurity programs, where human intelligence meets artificial intelligence.







