Healthcare Data: What it is and Why it’s Important to Protect it
Healthcare data is among the most sensitive categories of information. It includes electronic health records (EHRs), diagnostic images, genomic data, insurance information, billing records, prescription histories, biometric identifiers, and increasingly, real-time data generated by connected medical devices and wearable technologies. In 2026, healthcare data will become the digital backbone of modern medicine. Clinical decision-making, population health analytics, telemedicine, AI-assisted diagnostics, and personalized treatment plans all rely on continuous access to accurate, trusted data.
Yet that same reliance has expanded the healthcare attack surface to unprecedented levels. A compromised medical record can delay treatment, alter medication orders, disrupt surgeries, and erode public trust in healthcare institutions. While the convergence of cloud computing, artificial intelligence (AI), Internet of Medical Things (IoMT), and remote care has transformed healthcare delivery, it has also made the healthcare industry a prime target for cybercriminals seeking profit, disruption, and leverage.
Healthcare Is One of the Most Targeted Industries by Cybercriminals
Healthcare consistently ranks among the top three most attacked sectors globally, alongside finance and government.
Why Cybercriminals Target Healthcare Data
Healthcare organizations handle an abundance of high-value, sensitive personal data that remains useful indefinitely. Unlike credit card numbers, which can be cancelled, protected health information (PHI) cannot be altered and continues to hold value on underground markets. Complete medical records reportedly sell for up to $1,000 or more on dark web marketplaces due to their richness and permanence in identity theft and fraud operations. It’s no wonder that a June 2025 report from risk advisory firm Kroll highlighted that healthcare was the most breached sector in the previous year, accounting for 23% of all reported data breaches.
Healthcare data is uniquely valuable for the following reasons:
- High Black-Market Value: A single medical record can sell for 10–20 times more than a stolen credit card number on the dark web.
- Operational Urgency: Hospitals cannot afford downtime, making them more likely to pay ransoms.
- Fragmented Infrastructure: Many healthcare organizations operate legacy systems alongside modern platforms.
- Life-Critical Services: Cyber incidents directly impact patient care, increasing pressure on healthcare executives to comply with the demands of cybercriminals.
The Scale of Healthcare Cyberattacks
Recent data underscores the severity of the problem:
- 2024 marked the largest healthcare data breach year on record in the U.S., affecting over 276 million patient records.
- Ransomware attacks on healthcare providers increased by over 128% between 2020 and 2024.
- The average cost of a healthcare data breach reached $10.93 million, the highest of any industry.
- Over 60% of healthcare organizations experienced a cyberattack that disrupted patient care.
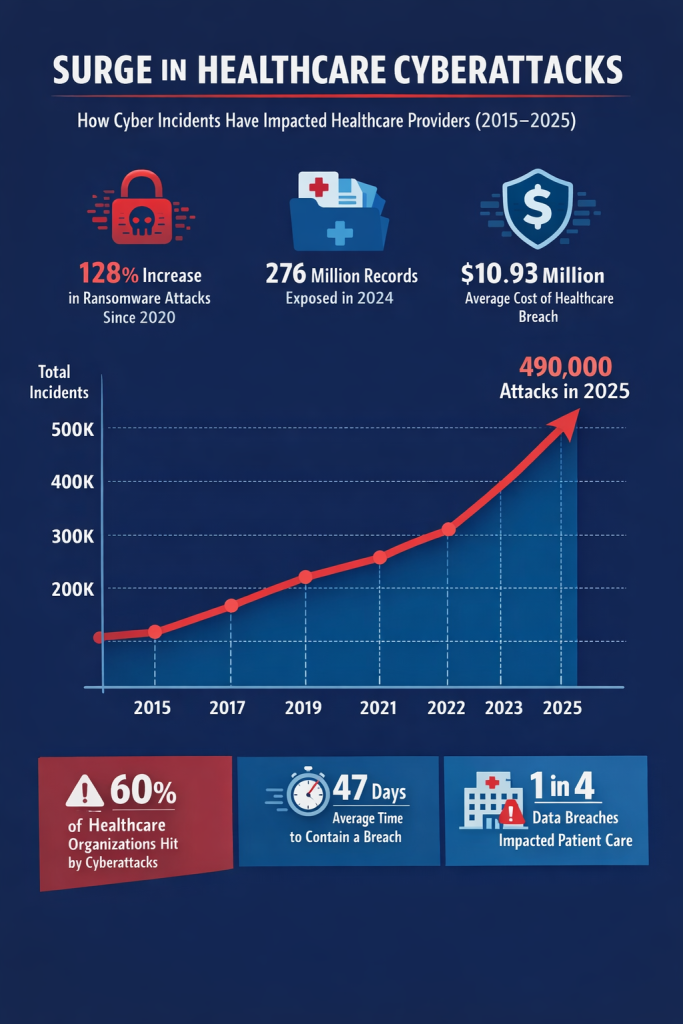
These real, quantifiable risks are why cybersecurity leaders in healthcare must continuously evolve their defenses and risk-mitigation strategies.
Modern Cybersecurity Risks Facing Healthcare in 2026
Healthcare’s digital transformation introduces both opportunities and risks. Below are the primary threats and their consequences:
1. Ransomware and Extortion
- Why it’s a risk: Ransomware-as-a-Service (RaaS) and extortion frameworks continue to democratize cyberattacks.
- Technological drivers: Remote access tools, third-party vendor systems, and poorly segmented networks.
- Consequences: System outages, compromised patient data, delays in clinical care, and massive recovery costs.
2. Cloud Misconfigurations and Data Exposure
- Why it’s a risk: The broad adoption of cloud services without mature governance can lead to accidental data exposure.
- Technological drivers: Misconfigured storage buckets, ambiguous IAM policies, and over-privileged accounts.
- Consequences: Large-scale PHI exposure, regulatory fines, and loss of patient trust.
3. Phishing and Social Engineering
- Why it’s a risk: Social engineering remains the leading initial access vector for breaches, including ransomware and credential theft.
- Technological drivers: Sophisticated email spoofing and customized AI-powered phishing.
- Consequences: Supply chain compromise, business email compromise, unauthorized access.
4. IoMT (Internet of Medical Things) Vulnerabilities
- Why it’s a risk: Connected medical devices such as insulin pumps, imaging machines, and cardiac monitors often lack robust security controls.
- Technological drivers: Rapid deployment without security-by-design, outdated firmware, and weak encryption.
- Consequences: Device manipulation, unauthorized network access, and patient safety risks.
5. Insider Threats
- Why it’s a risk: Employees, contractors, or third-party vendors with elevated privileges can leak or expose sensitive data.
- Technological drivers: Excessive permissions and inadequate monitoring.
- Consequences: HIPAA violations, data theft, and regulatory scrutiny.
Legal and Regulatory Imperatives for Securing Healthcare Data
Apart from ethical reasons, healthcare providers must secure data to comply with a complex regulatory environment.
Key Healthcare Regulations in the U.S.
- HIPAA (Health Insurance Portability and Accountability Act – Privacy and Security Rules): Requires administrative, physical, and technical safeguards for PHI. (Learn more)
- HITECH Act: Strengthens HIPAA enforcement and breach notification obligations. (Learn more)
- Proposed HIPAA updates (2025–2026): Aims to mandate multifactor authentication, encryption standards, and incident reporting.
- State Privacy Laws (e.g., California CPRA): Adds further protections for personal information, including health data.
Consequences of Non-Compliant Healthcare Providers
Violations can result in:
- Civil monetary penalties that can potentially reach millions of dollars per violation category annually under HIPAA structures.
- Mandatory breach notifications
- Class-action lawsuits
- Corrective action plans and audits
In 2026, regulators expect continuous risk management, incident response readiness, and documentation of security controls, not just periodic checklists.
Best Cybersecurity Practices & Tools for Healthcare Providers in 2026
Healthcare providers must treat cybersecurity as a core component of their IT infrastructure by implementing the following:
Strategic Cybersecurity Practices
- Zero Trust Framework (never trust, always verify)
- Continuous vulnerability and risk assessment
- Identity and Access Management (IAM) with least-privilege enforcement
- Segmentation of clinical and administrative networks
- Secure Software Development Lifecycle (SSDLC) for in-house and vendor tools
Essential Cybersecurity Tools
| Category | Tools |
|---|---|
| Identity Security | MFA, PAM, biometric authentication |
| Endpoint and Network Protection | EDR/XDR, microsegmentation |
| Data Security | Encryption, tokenization, DLP |
| Monitoring and Incident Response | SIEM, SOAR, UEBA |
| Compliance and Risk | GRC and audit platforms |
How Individuals Can Protect Their Healthcare Data
It’s not just healthcare providers who should prioritize data security. Patients and consumers also play a crucial role in securing their health information. Here are helpful steps individuals can undertake:
- Use unique, strong passwords on patient portals
- Enable multi-factor authentication wherever possible
- Review medical and insurance statements regularly for anomalies
- Avoid using public Wi-Fi for accessing health apps
- Be cautious of unsolicited health-related calls or emails
- Check privacy settings in health-related mobile apps
Why Cybersecurity Awareness Matters for Providers and Patients
- Human error is the most common cause of healthcare data breaches.
- Technological defenses can be overcome if healthcare employees aren’t trained to recognize cyber threats.
- Informed individuals who understand their rights and risks are more likely to identify suspicious activity.
A culture of cybersecurity awareness strengthens organizational resilience and preserves patient trust.
Healthcare Providers Need Cybersecurity Professionals More Than Ever
The healthcare data security landscape in 2026 is fundamentally different from what it was a decade ago. Cyber risks now threaten patient safety, operational continuity, regulatory standing, and institutional reputation simultaneously. This is why healthcare providers need cybersecurity professionals who are skilled at:
- Cyber risk management
- Regulatory compliance
- Medical device security
- Cloud and AI security
- Incident response in clinical environments
However, as is the case across industries, the demand for skilled cybersecurity professionals in healthcare far outpaces the supply of talent. This is where EC-Council University (ECCU) plays a vital role. As a trusted institution of cybersecurity education, ECCU equips learners with industry-aligned skills, expertise, and qualifications, empowering them to meet the cybersecurity workforce requirements of modern-day healthcare providers.
Find out how ECCU can help you become a job-ready cybersecurity professional:
FAQs About Healthcare Data Security in 2026
Healthcare records contain unique, unchangeable identifiers and comprehensive personal histories, making them highly valuable on illicit markets.
Phishing and ransomware are the top cyberattack vectors driving healthcare data breaches.
Yes. Many IoMT devices lack robust built-in security, making them vulnerable to remote exploitation.
U.S. providers must comply with HIPAA, HITECH, state privacy laws, breach notification rules, and evolving cybersecurity regulations.
Individuals should use strong passwords, Multi Factor Authentication (MFA), secure network practices, and regularly review their accounts.
Healthcare data breaches often take many months to identify and contain, increasing response costs.
While AI enables rapid, preemptive threat detection, it also powers more advanced, targeted cyberattacks.
Yes. Data breaches often lead to class-action lawsuits.
Online cybersecurity programs from EC-Council University will help you gain the essential skills, knowledge, and qualifications to become a data security expert.







