Cybercrime is a Daily Reality for Law Enforcement
In addition to traditional crimes, law enforcement agencies worldwide now routinely deal with ransomware attacks, online fraud, data breaches, and digital extortion. To respond effectively, cybersecurity has become a core operational function within current policing.
It enables the prevention, investigation, tracing, and prosecution of cybercriminals in today’s digital world.
Evolution of Cybercrime: Why Policing Had to Change
Early cybercrime involved:
- Simple website defacement
- Unauthorized system access
- Basic viruses and worms
Today, cybercrime is far more structured and advanced:
- Highly targeted ransomware campaigns
- AI-powered cyberattacks
- Large-scale phishing operations run like businesses
- Financial fraud using mule accounts and cryptocurrency
- Nation-state–sponsored espionage and sabotage
Attackers now operate across borders, use automation, and hide behind complex encryption. This evolution forced law enforcement to embrace cybersecurity as a crucial pillar of crimefighting.
How Cybersecurity Prevents Cybercrime
Prevention starts with visibility. Law enforcement uses cybersecurity tools to monitor digital environments for early warning signs of attacks continuously. This includes:
- Monitoring malicious domains and IP addresses
- Tracking phishing infrastructure
- Analyzing malware trends from past incidents
- Consuming threat intelligence feeds from trusted sources
Vulnerability assessment is another key area. Agencies and critical infrastructure providers perform regular security scans, identify exposed services and misconfigured systems, and patch known vulnerabilities before they are exploited.
Human behavior also remains a significant risk factor. To reduce this risk, law enforcement supports cybersecurity awareness programs for citizens, training for government employees, and educational campaigns on password hygiene and phishing detection.
Moreover, Law enforcement regularly coordinates with:
- Private cybersecurity firms
- Computer Emergency Response Teams (CERT) and Computer Security Incident Response Teams (CSIRT)
- Academic and research institutions
AI and data analytics also help detect abnormal patterns or activity that may indicate an ongoing cyberattack.
Digital Forensics: How Investigations Actually Happen
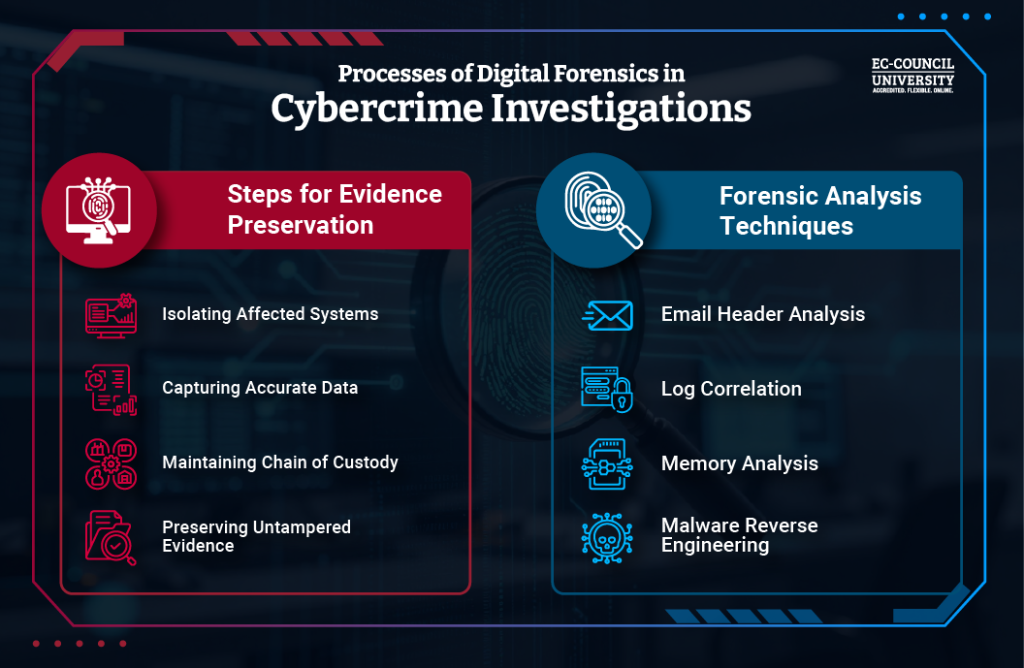
Once a cybercrime occurs, the focus shifts to digital forensics. The first step is evidence preservation. In this regard, investigators ensure:
- Systems are isolated correctly
- Data is captured without alteration
- Chain of custody is maintained
- Evidence is preserved without interference or tampering
Then comes forensic analysis, which involves examining laptops, mobile devices, servers, network traffic, firewall logs, cloud service logs, and access records.
Standard forensic techniques include:
- Email header analysis to trace phishing sources
- Log correlation to identify attacker movement
- Memory analysis to uncover running malware
- Malware reverse engineering to understand attacker intent
All findings are documented in a legally legitimate and verifiable manner.
Tracking Cybercriminals in Practice
Tracking cybercriminals isn’t just about finding a single IP address. It involves correlating multiple data points. To do this, investigators often use techniques such as:
- Network forensics to analyze traffic patterns
- IP reputation databases to link malicious activity
- Blockchain analysis tools to trace cryptocurrency payments
- Dark web intelligence to monitor criminal forums and marketplaces
OSINT (Open-Source Intelligence) plays a critical role as publicly available data helps to:
- Identify attacker aliases
- Link online personas across platforms
- Map relationships within cybercriminal groups
Since cybercrime rarely stays within the boundaries of one country, law enforcement also relies on:
- Interpol coordination
- Mutual legal assistance treaties (MLATs)
- Joint international cyber task forces
Legal and Regulatory Foundations
Cyber investigations must follow strict legal procedures. Key requirements include:
- Authorization for digital searches and seizures
- Compliance with cybercrime laws
- Respect for data protection and privacy regulations
Improper handling of evidence can invalidate an entire case. Hence, law enforcement must balance:
- Effective investigation
- Civil liberties
- Ethical use of surveillance technologies
Strong legal frameworks enable successful prosecution.
Cybersecurity Technologies Used by Law Enforcement
Cyber policing relies on a specialized technology stack. Common tools include:
- SIEM platforms for event correlation
- Threat intelligence platforms for attacker tracking
- Endpoint Detection and Response (EDR) tools
- Blockchain analytics for cryptocurrency tracing
- Cloud forensic tools for SaaS and IaaS environments
However, technology alone is not enough. Skilled cybersecurity professionals are also necessary. For that, cybersecurity certifications and structured programs, such as those offered by
EC-Council University (ECCU) can equip professionals with hands-on digital forensics skills, ethical hacking expertise, and a deep understanding of legal and compliance requirements essential for modern cyber law enforcement.
Cyber Challenges Faced by Law Enforcement
Even with advanced cybersecurity tools, law enforcement continues to face real challenges:
- Strong end-to-end encryption and anonymity technologies often restrict access to critical evidence.
- Cybercrime rarely respects borders, making cross-jurisdictional and legal coordination complex.
- Attack surfaces evolve faster than defense mechanisms.
- Many agencies struggle with limited resources and a shortage of skilled professionals.
Maintaining security without compromising individual privacy remains a constant balancing act.
The Future of Cyber Policing
Cybersecurity is reshaping law enforcement more than ever before. AI will assist investigators by automating log analysis and identifying hidden patterns in large datasets. Cyber ranges and simulation-based training will prepare professionals for real-world attacks. Stronger global intelligence sharing will improve response times and attribution. Above all, as cyber threats grow, so will the demand for qualified cybersecurity professionals.
Conclusion
Cybersecurity has become indispensable for modern-day law enforcement. It supports every stage of cybercrime response, from prevention and detection to investigation and prosecution. Effective cyber policing depends on skilled professionals, advanced technologies, and strong legal frameworks. Collaboration across governments, industry, and academia is critical. For students and professionals, cybersecurity offers a meaningful path to protect the digital society of tomorrow.
Learning digital forensics at ECCU opens pathways to impactful law enforcement careers. For more information:
About the Author
Ms. Prapti Patil is a cybersecurity professional and trainer with experience in hands-on security training and VAPT across web, mobile, API, and network environments. She is certified in CEH v13 (AI-integrated) from EC-Council, CPTE, CSA Level 1 & 2, and ISO/IEC 27001, and has collaborated with law enforcement agencies on real-world cybercrime investigations. Her expertise includes ethical hacking, AI-driven threat detection, OWASP Top 10, incident response, and compliance-driven security operations, with proven impact in reducing client risk through PoC-based remediation. She actively shares cybersecurity insights and awareness tips on her website – praptipatil.com







