INCIDENT HANDLING AND RESPONSE
10 Weeks
Duration
Online
Mode of Study
EC-Council Certified Incident Handler (ECIH)
Certification
$465
Cost Per Credit Hour
Course Overview
This course presents a structured approach for efficiently handling and responding to cybersecurity incidents. When such incidents occur, your role will be crucial in protecting your organization’s information and digital assets. You’ll minimize or eliminate potential harm to your organization by leveraging incident handling and response preparation, incident validation and prioritization, incident escalation and notification, forensic evidence gathering and analysis, incident containment, systems recovery, and incident eradication.
Your career prospects and earning potential will be enhanced by upgrading your know-how of the latest cybersecurity incident handling and response trends, tools, and techniques. You’ll also boost your professional credibility with a valuable cybersecurity certification – ECIH.


Admission Inquiry
"*" indicates required fields
Highlights of This Course

Cutting-Edge Courseware
10 modules featuring immersive video lectures and digital books for an in-depth understanding of every topic.

Virtual Labs
Simulate real-world scenarios for hands-on practice with the latest cybersecurity tools.

Quizzes
Engaging quizzes after each module that measure and reinforce your knowledge of the topics covered.

Discussions
Interactive discussion boards where you exchange ideas and views on the course topics with your peers and professors.

Essential Tools
Software tools that enhance your learning experience, such as Grammarly.

24x7 Online Library
Round-the-clock online library with an expansive collection of free-to-use learning resources.

Cybersecurity Certification
Includes EC-Council's industry-approved Certified Incident Handler (ECIH) certification.
Why Pursue a Career in Incident Handling and Response?
Market Growth
Soaring Demand
Earning Potential
Earning Potential
Weekly Modules
Week-1Module 1 – Introduction to Incident Handling and Response
This module introduces you to incident handling and response, focusing on identifying, analyzing, and mitigating security incidents.
Week-2Module 2 – Incident Handling and Response Process
In this module, you’ll learn about the key phases of the incident response lifecycle, including preparation, detection, containment, eradication, recovery, and post-incident analysis.
Week-3Module 3 – First Response
This module focuses on the critical first steps in incident response, ensuring swift and effective action to minimize damage. You’ll learn how to identify, assess, and contain security incidents while preserving evidence for further investigation.
Week-4Module 4 – Handling and Responding to Malware Incidents
This module shows you how to identify, contain, and mitigate malware incidents. You’ll learn about different types of malware, including viruses, ransomware, trojans, and spyware, as well as methods for detection and removal.
Week-5Module 5 – Handling and Responding to Email Security Incidents
This module focuses on identifying, mitigating, and preventing email-based security threats. You’ll learn to analyze phishing attempts, malware-laden attachments, business email compromise (BEC), and email spoofing.
Week-6Module 6 – Handling and Responding to Network Security Incidents
This module provides you with the knowledge and skills to detect, analyze, and respond to network security incidents. The module covers common network threats, including DDoS attacks, unauthorized access, man-in-the-middle attacks, and network intrusions.
Week-7Module 7 – Handling and Responding to Web Application Incidents
This module focuses on identifying, mitigating, and responding to security incidents targeting web applications. You’ll learn about common web threats, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and web defacement attacks.
Week-8Module 8 – Handling and Responding to Cloud Security Incidents
This module focuses on detecting, mitigating, and responding to security incidents in cloud environments. You’ll learn about cloud-specific threats, including misconfigurations, data breaches, account hijacking, and denial-of-service (DoS) attacks.
Week-9Module 9 – Handling and Responding to Insider Threats
This module focuses on identifying, mitigating, and responding to insider threats, which pose significant risks to organizations. You’ll learn about different types of insider threats, including malicious insiders, negligent employees, and compromised accounts.
Week-10Module 10 – Handling and Responding to Endpoint Security Incidents
This module focuses on detecting, mitigating, and responding to security incidents affecting endpoints, such as workstations, mobile devices, and servers. You’ll learn about common endpoint threats, including malware infections, unauthorized access, ransomware attacks, and insider threats.
What You Will Learn

- How to identify various types of cybersecurity threats
- Understanding attack vectors
- Understanding threat actors, their motives, goals, and objectives of their cyber-attacks
- The fundamentals of incident management and vulnerability management
- Threat assessment methodologies
- Risk management practices
- Incident response automation and orchestration
- Incident handling and response best practices and standards
- Cybersecurity frameworks
- Incident handling laws, acts, and regulations
- Steps involved in planning incident handling and response programs
- Computer forensics and forensic readiness
- The importance of first response and first response procedures
Virtual Lab Exercises

Get hands-on practice with state-of-the-art cybersecurity tools in simulations that mirror real-world scenarios. The virtual lab exercises included in this course cover incident handling disciplines like implementing policies using Group Policy Management Console, detecting missing security patches using MBSA on Windows, verifying image integrity, detecting phishing attacks, conducting vulnerability assessments using OSSIM, detecting SQL Injection and XSS attacks using dotDefender, and much more.
Skills You Will Gain
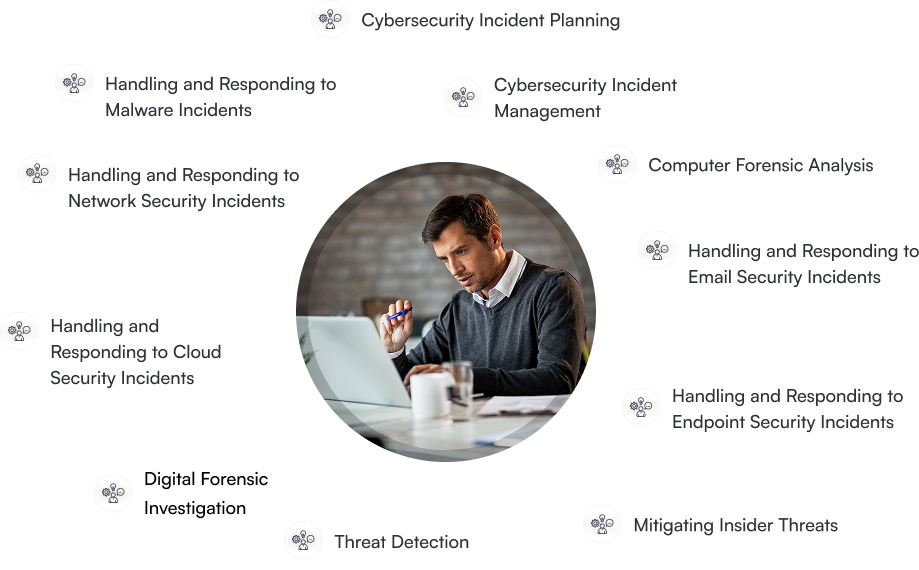

- Cybersecurity Incident Planning
- Cybersecurity Incident Management
- Handling and Responding to Malware Incidents
- Handling and Responding to Network Security Incidents
- Handling and Responding to Email Security Incidents
- Handling and Responding to Cloud Security Incidents
- Handling and Responding to Endpoint Security Incidents
- Mitigating Insider Threats
- Computer Forensic Analysis
- Digital Forensic Investigation
- Threat Detection
Jobs You Can Prepare For
Incident Handler
Total Course Fee
$1,395
- Cost Per Credit Hour: $465
- Technology Fee Per Term: $50
- Transcript Fee: $10 (plus shipping, if international)
Admission Criteria
- You must be aged 18 years or older.
- You must have a high school diploma (or equivalent), college degree, or relevant certification.
How to Apply
Step 01 :
Fill out the NDS application form and submit it to our Enrollment Advisor.
Step 02 :
Send us a scanned copy of your official government identification and documents showing proof of education.
Step 03 :
Pay the one-time $100 application fee.
Voices of Success: Hear from Our Alumni
Here’s what our students say about this incident handler certification course and how it helped advance their cybersecurity careers.
Frequently Asked Questions
What is a certified incident handler?
A certified incident handler is a professional qualified to manage and respond to cyber security incidents efficiently. The best way to become a certified incident handler is with EC-Council University’s Incident Handling and Response non-degree course, which provides the know-how to succeed in incident handling job roles.
What degree do you need to be an incident responder?
While a degree is not a strict requirement to get a job as a cyber security incident responder, it can be very helpful in enhancing your professional profile and distinguishing yourself from the competition. You can also gain a valuable competitive edge by earning the EC-Council Certified Incident Handler certification (ECIH) after completing EC-Council University’s Incident Handling and Response non-degree course.
