EXECUTIVE GOVERNANCE & MANAGEMENT
10 Weeks
Duration
Online
Mode of Study
Certified Chief Information Security Officer (CCISO)
Certification
$465
Cost Per Credit Hour
Course Overview
This course equips you with advanced expertise in audit management, governance, information security (IS) controls, human capital management, strategic program development, financial management, and more. You’ll take charge of safeguarding your organization’s data and technology ecosystem, directing policy, best practices, flow of operations, resource allocation, and overseeing every critical aspect of cybersecurity.
Your career prospects and earning potential will be enhanced as you acquire the skills and acumen needed to become a successful information security leader. You’ll also boost your professional credentials with a valuable cybersecurity certification – CCISO.


Admission Inquiry
"*" indicates required fields
Highlights of This Course

Cutting-Edge Courseware
10 modules featuring immersive video lectures and digital books for an in-depth understanding of every topic.

Virtual Labs
Simulate real-world scenarios for hands-on practice with the latest cybersecurity tools.

Quizzes
Engaging quizzes after each module that measure and reinforce your knowledge of the topics covered.

Discussions
Interactive discussion boards where you exchange ideas and views on the course topics with your peers and professors.

Essential Tools
Software tools that enhance your learning experience, such as Grammarly.

24x7 Online Library
Round-the-clock online library with an expansive collection of free-to-use learning resources.

Cybersecurity Certification
Includes EC-Council's world-renowned Certified Chief Information Security Officer (CCISO) certification.
Why Pursue a Career in Information Security?
Market Growth
Soaring Demand
Earning Potential
Earning Potential
Weekly Modules
Week-1Module 1 – Information Security Governance and Risk Management
This module provides an in-depth analysis of the core components of an effective information security governance program. You will explore governance frameworks, policies, and procedures that establish a robust security posture. You will also study the essentials of a comprehensive risk management program, covering key processes such as risk identification, assessment, and mitigation.
Week-2Module 2 – Executive Information Security Governance and Risk Management
This module offers an advanced understanding of information security governance and risk management. You will analyze the strategic components of governance programs, including frameworks, policies, and leadership roles that drive security initiatives.
Week-3Module 3 – Framework for Information Security Controls and Deployment
This module provides a comprehensive framework for deploying effective information security controls. You will explore foundational concepts and best practices for selecting, implementing, and managing security controls across various organizational environments.
Week-4Module 4 – Information Security Control Synthesis and Deployment
This module focuses on synthesizing the concepts of information security controls, their classification, and guidelines for effective deployment. You will gain a comprehensive understanding of various security controls, their classification based on function and application, and the attributes that make them effective in mitigating risks.
Week-5Module 5 – Management of Physical Access Controls in Compliance
This module focuses on implementing and managing physical access controls while ensuring compliance with relevant standards, laws, procedures, directives, policies, and regulations. You will examine the essential factors required to deploy and maintain physical access controls within organizational environments.
Week-6Module 6 – Physical Access Control and Security Mechanism
This module delves into the critical aspects of managing physical access controls while ensuring compliance with relevant standards, laws, procedures, directives, policies, and regulations. You will analyze various physical security mechanisms and their effectiveness in safeguarding network infrastructure.
Week-7Module 7 – IT Financial Management
This module is dedicated to IT financial management, equipping you with the skills to evaluate operational budgets within an IT department and design effective vendor selection processes and management policies. You will delve into budget oversight principles, cost management strategies, and financial planning techniques tailored to IT operations.
Week-8Module 8 – IT Budget Management and Vendor Governance
This module comprehensively explores IT budget management and vendor governance, which are essential for optimizing operational efficiency and strategic alignment within IT departments. You will learn to evaluate and manage operational budgets, focusing on cost allocation, financial forecasting, and resource optimization.
Week-9Module 9 – Security Operations: Incident Identification, Response, and Recovery
This module focuses on critical aspects of incident identification, response, and recovery within a security operations program. You will evaluate the key elements defining an organization’s ability to manage security events effectively.
Week-10Module 10 – Security Incident Management
This module focuses on security incident management, equipping you with the skills to evaluate and enhance an organization’s ability to identify, respond to, and recover from security events. You will study the essential elements of a robust security operations program, including incident detection methods, incident response planning, and recovery strategies.
What You Will Learn

- Components of an information security governance program
- Essentials of a risk management program
- Risk management processes
- Elements of a security operations program
- Concepts of information security controls
- Classifications of information security controls
- Guidelines to leverage information security controls
- Evaluating the operational budget of an IT department
- Vendor selection processes
- Cybersecurity management policy
- Countermeasures for safeguarding network infrastructure
Virtual Lab Exercises

Get hands-on practice with state-of-the-art cybersecurity tools in simulations that mirror real-world scenarios. The virtual lab exercises included in this course cover information security disciplines like penetration testing scoping and engagement methodology, fuzzing, Open-Source Intelligence (OSINT) methodology, social engineering penetration testing, bash environment and scripting, PowerShell scripting, and much more.
Skills You Will Gain
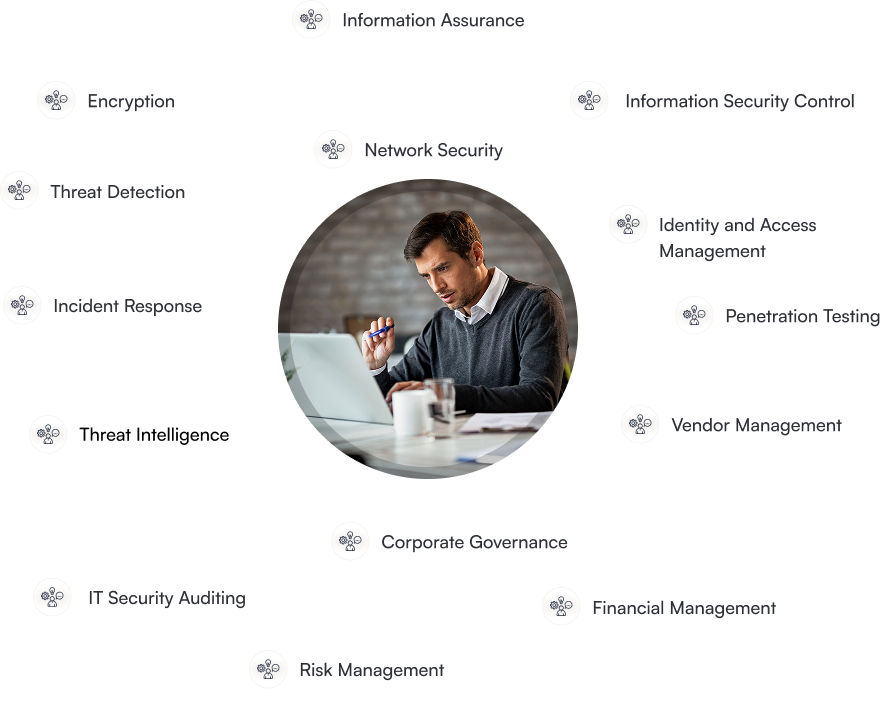

- Information Assurance
- Information Security Control
- Network Security
- Encryption
- Identity and Access Management
- Penetration Testing
- Threat Intelligence
- Incident Response
- Corporate Governance
- IT Security Auditing
- Risk Management
- Financial Management
- Vendor Management
Jobs You Can Prepare For
Risk Management Director
Total Course Fee
$1,395
- Cost Per Credit Hour: $465
- Technology Fee Per Term: $50
- Transcript Fee: $10 (plus shipping, if international)
Admission Criteria
- You must be aged 18 years or older.
- You must have a high school diploma (or equivalent), college degree, or relevant certification.
How to Apply
Step 01 :
Fill out the NDS application form and submit it to our Enrollment Advisor.
Step 02 :
Send us a scanned copy of your official government identification and documents showing proof of education.
Step 03 :
Pay the one-time $100 application fee.
Voices of Success: Hear from Our Alumni
Here’s what our students say about this course and how it helped advance their cybersecurity careers.
Frequently Asked Questions
What is a CCISO certification?
The CCISO certification is an executive-level certification designed to help professionals achieve C-level or senior leadership positions focusing on enterprise IT management and cyber security. The CCISO certification can pave the way toward job roles such as Chief Information Security Officer (CISO), Chief Technology Officer (CTO), IT Director, Director of Cybersecurity Operations, etc.
How much does the CCISO exam cost?
To attempt the CCISO exam, you must purchase the CCISO Voucher worth $999 from the EC-Council University Bookstore. This voucher covers the cost of the CCISO exam fee.
Is the CCISO certification worth it?
The CCISO certification is ideal if you want to advance to the highest levels of information security management and leadership in today’s business world. It enhances your ability to lead and manage an information security program, lending credibility to your cyber security and executive-level credentials. You’ll build skills in leadership and management, strategic planning, budgeting, risk management, compliance, corporate governance, and much more.
