ETHICAL HACKING AND COUNTERMEASURES
10 Weeks
Duration
Online
Mode of Study
Certified Ethical Hacker (CEH)
Certification
$465
Cost Per Credit Hour
Course Overview
This AI-powered ethical hacking course teaches you how cyber-criminals operate by illuminating their methods, tools, strategies, and motivations. You’ll outwit malicious actors by leveraging AI in ethical hacking and vulnerability assessment to develop effective countermeasures that protect organizations from sophisticated cyber-attacks.
Your career prospects and earning potential will be enhanced by upgrading your know-how of the latest ethical hacking trends, tools, and techniques. You’ll also boost your professional credibility with an in-demand cybersecurity certification – CEH v13.


Admission Inquiry
"*" indicates required fields
Highlights of This Course

Cutting-Edge Courseware
10 modules featuring immersive video lectures and digital books for an in-depth understanding of every topic.

Virtual Labs
Simulate real-world scenarios for hands-on practice with the latest cybersecurity tools.

Quizzes
Engaging quizzes after each module that measure and reinforce your knowledge of the topics covered.

Discussions
Interactive discussion boards where you exchange ideas and views on the course topics with your peers and professors.

Essential Tools
AI and other software tools that enhance your learning experience, such as Grammarly, ShellGPT, etc.

24x7 Online Library
Round-the-clock online library with an expansive collection of free-to-use learning resources.

Cybersecurity Certification
Includes EC-Council's industry-approved Certified Ethical Hacker (CEH v13) certification.
Why Pursue a Career in Ethical Hacking?
Market Growth
Soaring Demand
Earning Potential
Earning Potential
Weekly Modules
Week-1Module 1 – Ethical and Legal Considerations in Security Assessment and Penetration Testing
This module comprehensively explores the ethical and legal frameworks governing security assessments and penetration testing. You will learn about the critical ethical principles and legal regulations that guide these practices, including consent, privacy, and data protection laws.
Week-2Module 2 – Phases of Hacking and Ethical Hacking Strategies - I
This module delves into the various phases of hacking, providing a detailed examination of techniques used at each stage. You will explore network scanning and enumeration processes, understanding how hackers identify vulnerabilities and gather information.
Week-3Module 3 – Vulnerability Classification and Ethical Hacking Strategies
This module focuses on classifying vulnerabilities, threats, and attacks affecting information systems, emphasizing human-based, computer-based, and mobile-based risks. You will explore how these vulnerabilities impact system security and learn to categorize threats accordingly.
Week-4Module 4 – Phases of Hacking and Ethical Hacking Strategies - II
This module provides an in-depth examination of the different phases of hacking, focusing on how malware threats and sniffing techniques are employed to compromise information systems. You will analyze the various stages of a hacking attack, from initial reconnaissance to exploitation, emphasizing malware delivery and network sniffing methods.
Week-5Module 5 – Implementing Security Controls and Ethical Hacking Strategies
This module focuses on implementing appropriate levels of information security controls by analyzing evidence, information, and research findings. You will explore applying security measures effectively based on comprehensive data and threat analysis. The course will examine the different phases of hacking, particularly in the context of social engineering and denial-of-service (DoS) attacks.
Week-6Module 6 – Classification of Vulnerabilities and Countermeasures
This module classifies vulnerabilities, threats, and attacks across human-based, computer-based, and mobile-based dimensions of information systems. You will delve into session hijacking and methods for evading IDS, firewalls, and honeypots. By understanding how these specific attacks exploit system weaknesses, you will be equipped to identify and categorize various threats.
Week-7Module 7 – Hacking Techniques and Ethical Strategies
This module provides a comparative analysis of hacking techniques, assessments, and tools, focusing on web servers and applications. You will learn about the different phases of hacking, including the methods used to exploit vulnerabilities in web servers and applications.
Week-8Module 8 – Implementing Security Controls and Hacking Techniques
This module focuses on implementing appropriate information security controls by analyzing evidence, information, and research. You will delve into SQL injection and wireless network hacking techniques, learning how these methods exploit system vulnerabilities.
Week-9Module 9 – Advanced Hacking Techniques and Ethical Strategies for Mobile and IoT Systems
This module explores and contrasts various hacking techniques, assessments, and tools, focusing on mobile platforms, Internet of Things (IoT), and Operational Technology (OT) systems. You will examine different phases of hacking, from initial reconnaissance to exploitation, within the contexts of mobile platforms and IoT and OT environments.
Week-10Module 10 – Vulnerability Classification and Security Controls
This module focuses on classifying vulnerabilities, threats, and attacks across human-based, computer-based, and mobile-based dimensions of information systems, with particular attention to cloud computing and cryptography. You will analyze how these vulnerabilities manifest and impact system security within cloud environments and cryptographic implementations.
What You Will Learn

- Ethical and legal requirements of security assessment and penetration testing
- Strategies to comply with ethical and legal requirements
- Different hacking techniques, assessments, and tools
- Different vulnerabilities, threats, and attacks on information systems
- Countermeasure recommendations
- Different phases of hacking
- Ethical hacking strategies to secure various information system components
- Implementation of information security controls
- Evidence, information, and research-based security control
Virtual Lab Exercises

Get hands-on practice with state-of-the-art cybersecurity tools in simulations that mirror real-world scenarios. The virtual lab exercises included in this course cover ethical hacking disciplines like enumeration, vulnerability analysis, system hacking, malware threats, social engineering, denial-of-service, session hijacking, web server and application hacking, SQL injection, IoT and OT hacking, mobile platform hacking, cryptography, and much more.
Skills You Will Gain
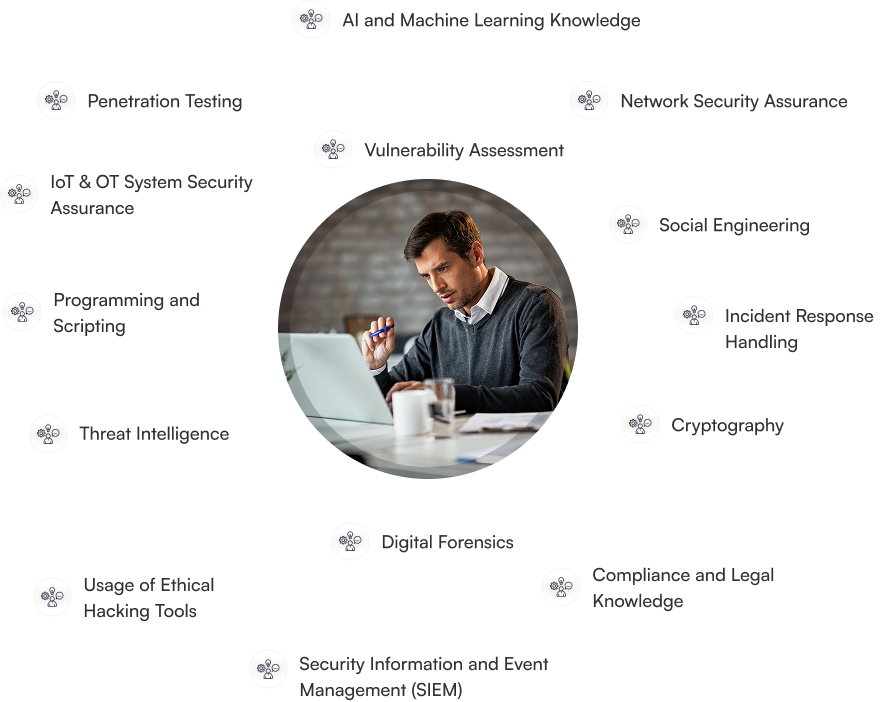

- AI and Machine Learning Knowledge
- Penetration Testing
- Network Security Assurance
- Cryptography
- Incident Response Handling
- Threat Intelligence
- Vulnerability Assessment
- Usage of Ethical Hacking Tools
- Security Information and Event Management (SIEM)
- IoT & OT System Security Assurance
- Programming and Scripting
- Social Engineering
- Compliance and Legal Knowledge
- Digital Forensics
Jobs You Can Prepare For
Penetration Tester (Pen Tester)
Ethical Hacker
SOAR Engineer
AI Security Engineer/Analyst/Consultant/Architect
Vulnerability Assessment Analyst
Solution Architect
Red Team Specialist
SIEM Threat Responder
Senior Cloud Security Analyst
Data Protection & Privacy Officer
IoT Security Engineer
Security Operations Center (SOC) Analyst
Machine Learning Security Specialist
Endpoint Security Engineer
AI/ ML Security Consultant
Crypto Security Consultant
… And Many More!
Total Course Fees
$1,395
- Cost Per Credit Hour: $465
- Technology Fee Per Term: $50
- Transcript Fee: $10 (plus shipping, if international)
Admission Criteria
- You must be aged 18 years or older.
- You must have a high school diploma (or equivalent), college degree, or relevant certification.
How to Apply
Step 01 :
Fill out the NDS application form and submit it to our Enrollment Advisor.
Step 02 :
Send us a scanned copy of your official government identification and documents showing proof of education.
Step 03 :
Pay the one-time $100 application fee.
Voices of Success: Hear from Our Alumni
Here’s what our students say about this course and how it helped advance their careers in ethical hacking.
Frequently Asked Questions
Is the Certified Ethical Hacker certification worth it?
The Certified Ethical Hacker (CEH) certification is valued throughout the cyber security industry because:
- The CEH certification is industry-approved and globally recognized.
- It makes you proficient in leveraging modern-day ethical hacking techniques and tools.
- The CEH certification gives you an in-depth understanding of network scanning, system hacking, malware threats, social engineering, and other critical aspects of ethical hacking.
- When hiring for ethical hacking positions, employers prefer candidates who possess the CEH certification.
How much do ethical hackers get paid?
There is a strong demand for ethical hacking professionals, resulting in lucrative pay packages for individuals skilled in this cyber security discipline. The yearly salary for an Ethical Hacker in the U.S. ranges between $127,000 to $141,500.
*Note: EC-Council does not guarantee the salary figures mentioned above. Factors like work experience, skill level, location, etc., influence the salary of ethical hackers.
How much does the CEH certification cost?
The Ethical Hacking and Countermeasures non-degree course from EC-Council University covers three (3) credit hours for $465 per credit hour ($1,395 total fee). After completing the course, you can earn the Certified Ethical Hacker (CEH) certification.
