How Veterans Can Use the GI Bill® to Launch Computer Science Careers
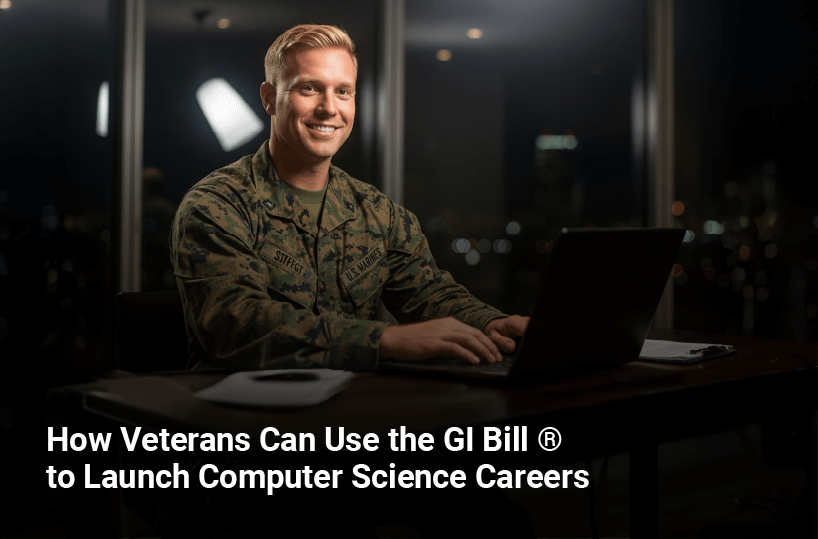
Using the GI Bill® to Remove Barriers to Higher Education Transitioning from military service to civilian life is a big step, but it’s also a powerful opportunity to build a new future. For many U.S. Military veterans, computer science offers a high-growth, high-impact career path that values the discipline, problem-solving, and leadership skills developed during […]
Why Is Cyber Security for Veterans an Ideal Career Path?

Looking to transition into the field of cyber security, but unsure if cyber security for veterans is the right choice? Well, you are not alone on this journey. Many veterans like you have stepped into this journey and moved forward successfully. As veterans, you bring experience, discipline, and a strong sense of duty. All the […]
GI Bill ® Eligibility: How to Qualify for GI Bill ® Education Benefits at EC-Council University

What Are GI Bill ® Education Benefits? If you’re a U.S. military veteran (or a dependent or spouse of a veteran) seeking to advance your education after serving the nation, the GI Bill ® can be your golden ticket. The GI Bill ® offers a set of education benefits provided by the U.S. Department of Veterans Affairs (VA) to […]
A Complete Guide to GI Bill® Education Benefits with EC-Council University

The United States owes its freedom and safety to the brave men and women who have served the country. EC-Council University (ECCU) deeply appreciates all the sacrifices made by the veterans for our country. As a gesture of gratitude, we are honored to support their journey with top-tier educational opportunities in cybersecurity. The U.S. Department […]
AI in Cybersecurity: Friend or Foe?

How Law Enforcement and Cybercriminals Are Both Using the Same Weapon Cybersecurity is no longer a game of defence and attack — it’s gotten much more complicated, and Artificial Intelligence (AI) is leading the way. While AI’s role in helping malicious actors carry out cybercrimes like creating manipulative deepfake videos, generating targeted phishing campaigns, and […]
