Cybersecurity Consultants: The Role They Play and How to Become One

As technology continues to advance and more organizations rely on digital systems, the need for cybersecurity has become increasingly important. Cybersecurity consultants play a critical part in supporting organizations to protect their systems and networks from cyberattacks. In this blog, we’ll explore the role of cybersecurity consultants and how you can become one. What is […]
How to Secure Your Home Wi-Fi Network from Hacker

Accelerated broadband speeds and considerate tariffs have made panicking about your data usage a thing of the past. But that does not suggest that you should disregard the Wi-Fi users. Determining who and what is on your network is more crucial than ever, whether you are at home or a small business user. People throughout […]
Don’t Be the Bait! Phishing Scams: How to Keep Your Online Identity Safe
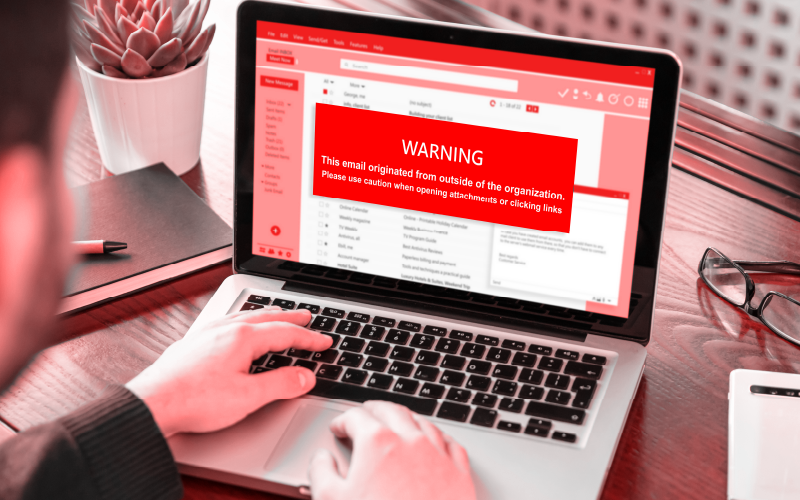
When it comes to devising innovative strategies to alienate hardworking people from their earnings, scammers can pivot on a dime. A “hook” for a phishing attempt can be created out of practically any news story, good or bad, whether it concerns a national or global natural disaster or the launch of a groundbreaking product or […]
Networking: Critical for Career Development in Cybersecurity

The cybersecurity community is comparatively small but tightly knit, which makes it essential that we establish and nurture a network. Your chances of acquiring an internship, securing your ideal career, or seeking an incredibly interesting volunteer opportunity might be determined by the people you make connections with. The significant role that security networking plays in […]
Top Skills Required for a Career in Cybersecurity

Are you considering a career in cybersecurity? With high median earnings, career possibilities across a range of industries, and a demanding, fast-paced work environment, cybersecurity is a highly sought-after, rapidly expanding area that needs competent individuals. If the idea of safeguarding organizations’ digital assets and intelligence from security breaches excites you, but you’re wondering if […]
