Relevance of the Dark Web in 2026
The dark web remains one of the most misunderstood yet consequential slices of the internet. To many, it’s an anonymous internet underworld, a haven for criminal activities, or simply a curiosity. To cybersecurity professionals, however, it is a dynamic ecosystem that directly affects digital security, national infrastructure, individual privacy, and economic stability. While it accounts for only a tiny fraction of the global web, its effects reverberate through mainstream cyberspace via stolen data, malware distribution, ransomware negotiations, and illicit financial networks.
This article examines the most significant facets of the dark web while also emphasizing the need for a thorough understanding of it to achieve practical cybersecurity expertise.
What Is the Dark Web and How Does It Function?
The dark web refers to encrypted sections of the internet that standard search engines do not index and that require specialized tools for access. The most common gateway is the Tor network, which anonymizes users’ online actions by routing them through multiple volunteer-run servers worldwide. Unlike the surface web (the parts of the internet accessible via Google, Bing, and other search engines), or even the deep web (password-protected sites such as banking portals), the dark web intentionally obscures identities and locations. This is achieved through protocols like Tor, I2P, and Freenet.
Key features of dark web functionality include:
- Onion routing: Encrypts internet traffic in layers, making it difficult to trace users or hosts.
- Cryptocurrency transactions: Bitcoin and other digital currencies facilitate anonymous transactions without intermediaries.
- Hidden services: Sites with addresses not indexed by standard search engines but accessible through Tor or similar software.
The result is a shadowy ecosystem with both innocuous and criminal applications, all of which are protected by anonymity.
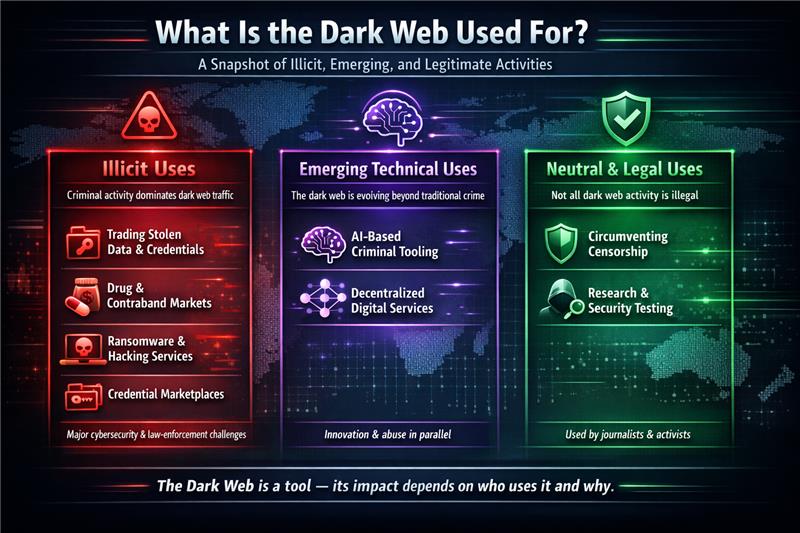
What Is the Dark Web Used For?
While illegal markets dominate headlines, the dark web’s uses in 2026 span a spectrum:
Illicit Uses
- Trading stolen data and credentials: Around 60% of dark web activity in 2025 involved trading stolen credentials and breached data.
- Drug and contraband markets: Underground markets still conduct high-value transactions in illegal drugs and goods, with estimates placing drug sales in the hundreds of millions annually.
- Ransomware and hacking services: Cybercrime forums sell ransomware-as-a-service tools, malware kits, and hacking tutorials.
- Credential marketplaces: Theft and resale of login credentials for banks, email, and streaming accounts fuel fraud industries.
Emerging Technical Uses
- AI-based criminal tooling: Illicit actors increasingly sell AI-assisted malware, phishing scripts, and voice impersonation kits, with year-over-year growth of 45% to 70% in some categories.
- Decentralized digital services: Blockchains and smart contract marketplaces are used for trustless dark web commerce.
Neutral and Legal Uses
- Circumventing censorship: Activists, journalists, and citizens in oppressive regimes use the dark web to communicate safely.
- Research and security testing: Academic researchers and penetration testers use dark web tools for threat analysis and vulnerability assessments.
Despite its small size (comprising only about 0.01% of the total global web), the dark web attracts millions of daily users seeking privacy or illicit services.
Dangers and Risks of the Dark Web
The anonymity afforded by the dark web also enables criminal and harmful behavior. These represent profound risks to individuals, businesses, and global security.
- Exposure to Malware and Cybercrime: Visiting dark web sites exposes users to trojans, keyloggers, ransomware, and other malware. Cybercriminals embed malicious files in downloads to compromise devices.
- Identity Theft and Data Abuse: Compromised personal data, such as email credentials, social security numbers, and financial information, is routinely sold in dark web markets.
- Facilitation of Organized Crime: Forums and marketplaces provide infrastructure for illegal arms deals, drug trafficking, human trafficking, and weapon distribution.
- Extremism and Violence: Some dark web websites are used to organize extremist groups, fund violent acts, or disseminate harmful propaganda. Recent arrests have linked dark web activity to ordered threats against political figures.
- Hidden Abuse and Exploitation: The dark web can sadly serve as a space for abusive communities, such as child exploitation networks, which thrive in anonymity.
Positive Aspects of the Dark Web
Despite its negative reputation, not all dark web activity is illegal or harmful.
- Digital Privacy and Free Expression: For whistleblowers, political dissidents, journalists, and citizens under repressive governance, dark web technologies like Tor provide vital protection from surveillance.
- Research and Cyber Defense Development: Cybersecurity professionals monitor dark web forums for threat intelligence, learning about emerging malware, tactics, and stolen data trends to defend networks proactively.
- Academic and Ethical Studies: Scholars use controlled access to study cybercrime ecosystems to inform law enforcement and defense strategies.
Recent Real-World Instances of Dark Web Usage
- Politically Motivated Threat Network: In November 2025, a man was arrested in Germany for operating a dark web site soliciting donations to finance assassination attempts against politicians; the site also provided instructions on making explosives. (Source: Reuters)
- Massive Data Leak Monitoring: In late 2025, Proton launched a Dark Web Data Breach Observatory that tracked nearly 800 breaches involving more than 300 million records, demonstrating the dark web’s role in ongoing data leakage and resale. (Source: Lifewire)
- Child Exploitation Networks: Investigations in 2025 exposed widespread child predator communities on the Tor network, used to share exploitative material and grooming tools. (Source: The Guardian)
Cybersecurity Implications of the Dark Web
The dark web’s influence on cybersecurity in 2026 is broad:
- Threat intelligence: Security teams harvest dark web insights to anticipate attacks and patch vulnerabilities.
- Incident response: Data breach detection often starts with a dark web signal that credentials are being traded.
- Fraud prevention: Credential theft spotted on dark markets informs authentication policy changes.
- Law enforcement collaboration: International takedowns of forums and ransomware services rely on combined cyber ops.
Understanding dark web tools is now a crucial part of defending cloud infrastructure, IoT, AI systems, and critical infrastructure, especially as AI-powered cybercrime tools proliferate.
Why Cybersecurity Professionals Must Understand the Dark Web
Developing a strong understanding of the dark web is no longer optional, as it has become a central component of modern cybersecurity.
- Predict, Not Just Respond: Knowledge of dark web trends lets defenders anticipate criminal strategies before they hit mainstream systems.
- Protect Sensitive Assets: Understanding where and how stolen data circulates allows organizations to harden security preemptively.
- Support Risk Mitigation: Identifying threat actors and malware kits through dark web monitoring can significantly shorten incident response time.
Cybersecurity professionals should view the dark web as a strategic battleground where attacks are planned and cybercrime tools are traded.
Education Is Key to Combating Dark Web Cybercrime
As cyber threats become increasingly automated with the aid of AI and data spreads faster than ever, future-focused cybersecurity certification courses and degree programs, such as those offered by EC-Council University (ECCU), have incorporated dark web intelligence, legal frameworks, and defensive analytics into curricula. Professionals who master insights into the dark web will be better equipped to defend digital networks more effectively, shape robust cybersecurity policies, utilize appropriate tools and techniques to combat advanced cyberattacks, and raise public awareness to mitigate harm. The solution is not to ignore or ban the dark web. It is to educate defenders, empower ethical use, and develop resilient systems that make cybercrime less potent.
Reach out to us for more information on cybersecurity education at ECCU:
Commonly Asked Questions About the Dark Web
No. The deep web includes any non-indexed content (like bank accounts), whereas the dark web refers specifically to anonymized, encrypted sections accessed via Tor and similar tools.
Yes, through digital forensics, undercover operations, blockchain analysis, and international cooperation, authorities can sometimes identify users despite their use of anonymity.
Use unique passwords, enable multi-factor authentication, and monitor breach alerts from reputable services.
Yes. Journalists, activists, and researchers often use it for privacy protection or threat research.
Yes, AI tools and automated breach propagation have accelerated the development of criminal technology, and even consumer monitoring tools (such as Google’s dark web report) are being retired in 2026, shifting the focus toward proactive security practices.







