What Is Cyber Incident Response?
At its core, cyber incident response is a structured, strategic approach to containing cyber-attack incidents and preventing them from escalating. The process involves cyber incident specialists actively detecting, investigating, containing, and executing recovery plans following cyberattacks or security breaches. The incident response process is not just a technical exercise, but a well-planned and coordinated exercise executed across people, processes, and technology to preserve operations, protect data, and maintain trust.
Unlike the general cybersecurity practices, incident response kicks into gear after a threat is detected, guiding teams through the chaos of an actual attack so that damage is minimized, and recovery is swift and controlled.

Why Incident Response Matters?
- Regulatory penalties and compliance challenges
- Operational downtime that disrupts customers and stakeholders
- Reputational damage with long-term brand impact
Real-World Cyber Incident: How Did the Incident Response Strategies Shape the Outcome
The Case of St. Paul Ransomware Attack and the Incident Response in 2025
One of the most significant U.S. cyber incidents in 2025 involved the City of St. Paul, Minnesota, which suffered a coordinated ransomware attack that disrupted government services and triggered an unprecedented response.
What Happened
On July 25, 2025, St. Paul’s city networks experienced suspicious activity that was quickly confirmed as a deliberate, coordinated ransomware attack targeting municipal systems. Critical internal services, including online payments, public Wi-Fi, and internal applications, were entirely disrupted.
Immediate Incident Response Actions
The city officials immediately activated their incident response plan, which involved:
- Rapid Detection & Escalation: Suspicious activity was identified early on July 25, enabling the IT team to begin investigative triage without delay.
- Defensive Shutdown: By July 27, after confirming malicious behavior, all city information systems were proactively shut down to prevent the attack from escalating further across networks.
- Federal Support: Recognizing the severity and complexity of the incident, St. Paul engaged the FBI to assist with containment and forensic investigation, demonstrating the value of government partnerships in high-impact incidents.
- National Guard Cyber Assets Activated: The Governor of Minnesota authorized the deployment of the National Guard’s cyber protection assets, strengthening the city’s technical capabilities and accelerating response time.
Recovery & Resilience
- Isolation Over Ransom: St. Paul chose not to pay the ransom and instead implemented defensive isolation and systematic recovery, limiting financial loss and discouraging future exploitation.
- Password Reset Campaign: To eliminate residual access, city IT teams conducted a large-scale password reset campaign for approximately 3,500 employees, requiring rapid coordination and secure physical infrastructure to manage the process.
Why This Case Matters
The St. Paul incident is a powerful, real-world example of how a structured incident response plan, from early detection and containment to decisive recovery actions, can reduce damage and restore services efficiently.
Rather than letting the attack cripple city services indefinitely, leaders combined strategy, technical controls, and external collaboration to regain control.
The incident reflects the core principle in incident response, which is not about just preventing an attack escalation, but managing it intelligently and resiliently, a skillset developed through strategic training and preparedness.
As threats evolve to be more complex and sophisticated, cyber professionals who understand the full lifecycle of incident management, including detection, containment, coordination, and recovery, are in high demand. Programs such as a Master of Science in Cybersecurity with a specialization in Incident Management and Cyber Operations help prepare individuals to lead these complex responses with confidence and strategic foresight.
What Are the Key Roles of an Incident Response Team
Successful incident response depends on clearly defined roles of every incident response team member, including:
- Incident Response Manager: Coordinates response efforts and decision-making.
- SOC Analysts: Monitor alerts and investigate suspicious activity.
- Threat Hunters: Proactively search for hidden threats.
- Digital Forensics Specialists: Analyze compromised systems and preserve evidence.
- IT & Cloud Engineers: Support system isolation and recovery.
- Legal & Compliance Advisors: Ensure regulatory and legal obligations are met.
These roles work together to manage cyber incidents and their responses efficiently and effectively.
A Step-by-Step Guide to the Incident Response Lifecycle
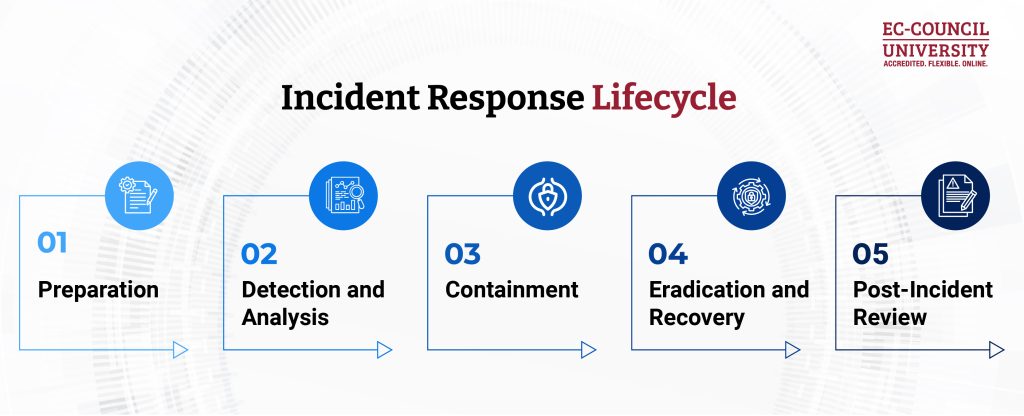
1. Preparation: Building Readiness Before an Attack Occurs
Preparation is a strategic phase built to equip you to face cyber-attacks or incidents well in advance, before they strike. This phase is the foundational pillar of every successful incident response program. It is a phase wherein organizations define incident response policies, assign clear roles and responsibilities, establish communication protocols, and ensure teams have access to the right tools and training.
The stage often includes:
- Developing and testing incident response playbooks
- Conducting tabletop exercises and simulations
- Ensuring logging, monitoring, and alerting systems are properly configured
Strong preparation enables teams to act decisively under pressure—rather than scrambling during a real crisis.
2. Detection and Analysis: Identifying and Understanding the Threat
Once suspicious activity is detected, the focus shifts to determine whether it represents a genuine security incident. Analysts examine alerts, logs, and threat intelligence to understand what happened, how it happened, and the severity of the incident.
Technologies such as SIEM, EDR, and network security monitoring tools are critical for early threat detection. The tools help teams reduce the dwell time and prevent attackers from escalating their access. Accurate analysis ensures that response efforts are proportionate and targeted, not rushed or misdirected.
3. Containment: Stopping the Damage from Spreading
Containment of an attack involves efforts to limit the incident’s impact while preserving evidence collected during the investigation for future use.
Depending on the situation and level of adversity, the process may involve isolating infected systems, deactivating compromised accounts, blocking malicious IP addresses, or segmenting networks.
Effective containment balances speed with caution—stopping the threat quickly without disrupting critical business operations unnecessarily.
4. Eradication and Recovery: Removing the Threat and Restoring Operations
After containment, the team focuses on eliminating the attacker’s presence from the environment. At this stage, the process and strategy include removing malware, closing exploited vulnerabilities, patching systems, and validating that no backdoors remain.
The recovery phase follows the eradication stage and involves restoring systems from trusted backups, monitoring for signs of reinfection, and gradually returning systems to operation and normalcy. The goal is to resume normal operations securely and confidently, not simply quickly.
5. Post-Incident Review: Learning, Improving, and Strengthening Defenses
Incident response doesn’t just end at the recovery stage when systems are back online. A thorough post-incident review is essential to understand what worked, what didn’t, and how to improve when such incidents occur.
The post-incident review phase typically includes:
- Root cause analysis
- Documentation of response actions
- Updating of policies, controls, and security training
Documenting the processes, response actions, and lessons learned, organizations can turn real-world incidents into opportunities to improve their security posture and preparedness for future threats.
How to Build an Effective Incident Response Plan
For organizations wondering how incident response works in cybersecurity, it starts with a strong plan. An effective incident response strategy involves several critical common threads, which include:
- Contain quickly to prevent escalation
- Collaborate with law enforcement and experts
- Communicate transparently with stakeholders
- Use lessons learned to strengthen defenses
Connecting the threads for an effective incident response requires execution of an established incident response plan. Below is a breakdown of best practices for an incident response plan:
- Defining clear escalation paths and communication protocols
- Creating tested IR playbooks for common attack scenarios
- Integrating incident response with business continuity plan
- Conducting regular tabletop exercises
- Aligning security initiatives with recognized frameworks such as NIST
An effective plan ensures faster decision-making and reduces chaos during high-pressure incidents.
What Are the Different Tools and Techniques Used by the Incident Response Teams
Modern incident response depends on a combination of technology and expertise:
- SIEM (Security Information & Event Management) for centralized threat detection and alerts
- Endpoint Detection & Response (EDR) to investigate and contain endpoint threats
- Security Orchestration and Automation (SOAR) for faster, automated, and consistent response playbooks
- Threat Intelligence Feeds to stay updated and aware of emerging attack vectors
These tools, paired with trained analysts, help shorten breach lifecycles and keep business operations running smoothly.
The Future of Incident Response: AI, Expertise & Operations
Cyber incident response isn’t just about responding when something goes wrong. It is more about being ready when an incident occurs, and your organization remains resilient, trusted, and secure. With a thoughtful strategy, the right tools, and continuous learning, you can turn cyber adversity into a source of strength.
With the cybersecurity landscape continuing to evolve and increasingly adopting cloud technologies, AI-driven attacks, and increasingly sophisticated adversaries, these threats are becoming rampant. In response to this successful incident, responders are combining automated detection with expert analysis to stay ahead of threats.
That’s why developing relevant skills in incident management and cybersecurity operations is valuable today. Advanced cybersecurity programs like the Master of Science in Cybersecurity with a focus on Incident Management and Cyber Operations equip professionals with the technical expertise, strategic thinking, and operational readiness needed to lead in crises.
How You Can Prepare for Incident Response and Management with EC-Council University
EC-Council University (ECCU) emphasizes real-world readiness by focusing on:
- Mastering in-demand technical expertise in network security, ethical hacking, penetration testing, and more
- Building hands-on practical skills in incident handling, threat analysis, incident response, and recovery
- Developing strategic management and decision-making skills in incident scenarios
- Sharpening soft skills such as communication, leadership, decision-making, problem-solving, and critical thinking
This academic approach helps students understand what happens during an incident response, bridging theory with operational practice.
If you are looking to specialize in cyber incident response and build practical expertise in incident management and cyber operations, explore the Master of Science in Cybersecurity – Incident Response specialization or a Graduate Certificate Program focused on Incident Management and Business Continuity at ECCU. Pursuing this degree can be a powerful next step in your cybersecurity journey.







